Tor Browser: Ever felt like Big Brother is watching your every online move? Want to browse the web without leaving a digital footprint the size of Texas? Then you need to know about Tor. This powerful browser routes your internet traffic through a network of volunteer-run servers, making it incredibly difficult to track your activity. Think of it as a super-secret, encrypted tunnel through the internet – perfect for protecting your privacy and accessing content that might be blocked in your region.
We’ll dive into how it works, its strengths and weaknesses, and everything you need to know to use it safely and effectively.
We’ll cover the nuts and bolts of Tor’s architecture, exploring its layered onion-routing system and how it keeps your browsing habits private. We’ll also tackle the security implications, addressing potential vulnerabilities and offering tips to maximize your anonymity. Plus, we’ll compare Tor to other privacy tools, like VPNs, and discuss its role in bypassing censorship. Get ready to become a Tor ninja!
Tor Browser Functionality
Tor Browser is a free and open-source browser designed to enhance your online privacy and security. Unlike regular browsers, Tor routes your internet traffic through a series of volunteer-operated servers, creating a layered network that obscures your IP address and makes it significantly harder to track your online activity. This makes it a powerful tool for accessing websites and services that might be blocked or monitored in your region, or for simply protecting your personal information from prying eyes.Tor’s core function is anonymizing your internet traffic.
It achieves this through a process called onion routing. Your data is encrypted and sent through multiple relays, each only knowing the address of the relay before and after it. This prevents any single point from knowing both your origin and destination, making it extremely difficult to trace your activity back to you.
Anonymizing Web Traffic Using Tor
The anonymization process begins when you initiate a connection to a website. Your request is encrypted and sent to the first relay in the circuit, chosen randomly from Tor’s network. This relay decrypts a portion of the encryption, re-encrypts it, and forwards it to the next relay. This process continues until the request reaches the final relay, the exit node, which sends the request to the target website.
The response follows a similar path in reverse, with each relay decrypting and re-encrypting the data before passing it along. The entire process is like an onion, with layers of encryption peeled away at each step, hence the term “onion routing.”
Tor’s Protection of User Privacy
Tor protects user privacy by preventing your internet service provider (ISP), the websites you visit, and potential eavesdroppers from easily linking your online activity to your identity. While Tor doesn’t offer complete anonymity (exit nodes can potentially see your destination), it significantly increases your privacy compared to using a standard browser. This enhanced privacy is particularly beneficial for individuals who are concerned about government surveillance, corporate tracking, or online harassment.
For example, a journalist in a repressive regime might use Tor to communicate with sources without fear of their communications being intercepted and traced back to them.
Setting Up Tor Browser for the First Time
Setting up Tor Browser is straightforward. Here’s a step-by-step guide:
- Download the Tor Browser from the official Tor Project website. Ensure you download from the official source to avoid malicious software.
- After downloading, run the installer. The process is similar to installing any other application on your computer. Follow the on-screen instructions.
- Once installed, launch the Tor Browser. The browser will take a few moments to connect to the Tor network. You’ll see a status message indicating the connection progress.
- Once connected, you’re ready to browse the web anonymously. Remember that while Tor enhances your privacy, it’s not foolproof. Avoid using your real name or other personally identifiable information online, and be mindful of the websites you visit.
Tor Network Architecture
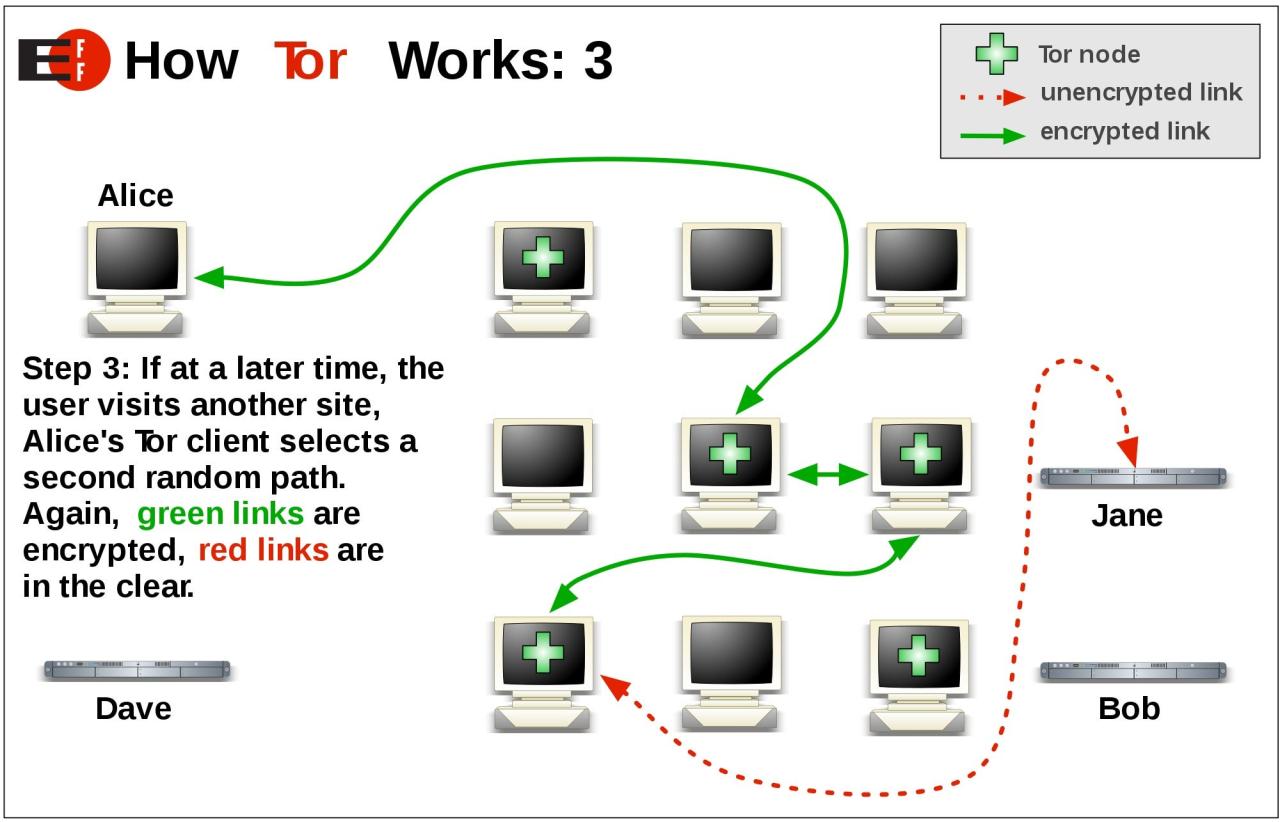
Okay, so Tor’s architecture isn’t exactly rocket science, but it’s pretty clever. It’s all about layering security to keep your browsing private. Think of it like a series of encrypted tunnels, each one adding another layer of protection. The more layers, the harder it is to trace your activity back to you.The Tor network uses a layered approach, routing your traffic through multiple relays before it reaches its final destination.
This multi-layered system is the key to Tor’s anonymity. Instead of a direct connection, your data bounces around the network, making it extremely difficult to track the origin of the request. Each layer adds another layer of encryption, making it much harder for anyone to see what you’re doing.
Tor Network’s Layered Structure
Imagine your data packet as a letter traveling through a series of post offices. Each post office (relay) only knows where to send the letter next, not where it came from or where it’s ultimately going. This is crucial for anonymity. The letter is also encrypted at each step, so even if someone intercepts it, they can’t read it.
The final post office, the exit node, sends the letter to its final destination. This whole process ensures that your connection remains masked and secure.
Simplified Diagram of Data Path Through Tor
Let’s visualize this. Imagine three relays: A, B, and C. Your computer (let’s call it “You”) initiates a connection to a website. Your request is first encrypted and sent to relay A. Relay A only sees the encrypted message and the address of relay B.
It forwards the encrypted message to B. Relay B, similarly, only sees the encrypted message and the address of relay C. Finally, relay C, the exit node, decrypts the last layer of encryption and sends the request to the website. The response follows the same path in reverse, with each relay decrypting its layer of encryption. The website only sees the IP address of the exit node, not your actual IP address.
Comparison to Other Anonymizing Networks
Tor’s architecture differs from other anonymizing networks in its emphasis on decentralized relays and layered encryption. Unlike VPNs which route all traffic through a single central server, Tor utilizes a distributed network of volunteer-operated relays. This makes it much more resilient to attacks and censorship. Other anonymizing networks may offer different levels of security and anonymity, depending on their architecture and implementation.
For instance, some might rely on more centralized servers, making them potentially more vulnerable.
The Role of Tor Relays and Exit Nodes
Tor relays are the backbone of the network. They forward encrypted traffic between other relays, obscuring the origin of the data. Each relay only knows the address of the next relay in the chain, maintaining the anonymity of the user. The exit node, on the other hand, is the final relay that sends the decrypted data to the destination website.
This is a critical point because the exit node can potentially see the unencrypted data. While Tor aims to select exit nodes randomly, this remains a potential vulnerability. It’s important to be aware that the website you are accessing can see your traffic once it leaves the exit node.
Security and Privacy Implications

Using Tor, while offering a significant boost to your online privacy, isn’t a foolproof solution. It’s crucial to understand its limitations and potential vulnerabilities to use it effectively and safely. Think of it like a really strong lock on your front door – it significantly improves security, but it’s not invincible against determined attacks.
Tor’s architecture, while designed to obfuscate your online activity, presents several points of potential weakness. The anonymity it provides is relative, not absolute. Understanding these weaknesses allows for the implementation of best practices to mitigate risks and maximize the privacy benefits Tor offers.
Potential Security Vulnerabilities
Tor’s security relies on several factors, and weaknesses in any of these can compromise your anonymity. Exit nodes, for example, can be compromised, allowing malicious actors to intercept your traffic. Furthermore, vulnerabilities within the Tor Browser itself or your operating system can be exploited to leak information. Even seemingly minor issues like running outdated software or visiting malicious websites can significantly reduce the effectiveness of Tor.
The network’s reliance on volunteer-run nodes also introduces the possibility of compromised relays.
Best Practices for Enhancing Security While Using the Tor Browser
While Tor offers robust privacy features, enhancing your security requires proactive measures. It’s a layered approach, combining the strength of Tor with careful user habits.
- Keep your Tor Browser updated: Regular updates patch security vulnerabilities, ensuring your protection against the latest threats.
- Use strong passwords and two-factor authentication (2FA) wherever possible: This adds an extra layer of security to your accounts, even if your Tor session is compromised.
- Avoid using plugins or extensions: Extensions, while convenient, can introduce vulnerabilities and compromise your anonymity.
- Be cautious of phishing attempts: Phishing scams can target Tor users, attempting to steal your credentials or personal information. Always verify the authenticity of websites before entering sensitive data.
- Use HTTPS Everywhere: This browser extension encrypts your connection to websites that support HTTPS, adding an extra layer of security.
- Regularly clear your browser history and cookies: This minimizes the risk of information leakage if your browser is compromised.
- Use a VPN in conjunction with Tor (with caution): While not always recommended, using a VPN in front of Tor can offer additional protection in certain situations, but careful selection of a trustworthy VPN provider is crucial. Using an untrustworthy VPN can negate the benefits of Tor.
Limitations of Tor in Providing Complete Anonymity
It’s important to understand that Tor doesn’t guarantee complete anonymity. While it significantly obscures your online activity, certain factors can still expose your identity. The inherent trust in exit nodes, the possibility of network analysis, and the potential for metadata leakage all contribute to these limitations.
- Exit Node Compromise: Malicious actors controlling exit nodes can intercept your data.
- Traffic Analysis: While Tor obscures the path of your traffic, sophisticated analysis might still reveal patterns and potentially identify you.
- Metadata Leakage: Information like your operating system, browser version, and the timing of your connections can leak, potentially revealing clues about your identity.
- Poor OpSec: User error, such as visiting untrusted websites or revealing personal information, undermines the anonymity Tor provides.
Potential Threats and Countermeasures
A variety of threats can compromise your security when using Tor. Implementing countermeasures is crucial to minimize these risks.
| Threat | Countermeasure |
|---|---|
| Malware on your system | Keep your operating system and applications updated, use a reputable antivirus program. |
| Compromised exit nodes | Be cautious about sensitive activities on Tor; avoid accessing banking or highly sensitive information. |
| Network surveillance | Use Tor in conjunction with other privacy-enhancing techniques (with caution). |
| Phishing attacks | Be vigilant about suspicious links and websites; verify authenticity before entering any sensitive information. |
| Deep packet inspection | Minimize metadata leakage by avoiding revealing information about your online behavior. |
Legal and Ethical Considerations
The use of Tor, while designed to protect privacy, presents a complex interplay of legal and ethical considerations. Its inherent ability to anonymize online activity makes it a double-edged sword, capable of shielding both legitimate users and those engaged in illegal activities. Understanding these implications is crucial for navigating the ethical and legal landscape surrounding Tor’s use.
Legal Implications of Using Tor for Illegal Activities
Using Tor to engage in illegal activities like drug trafficking, money laundering, or accessing child sexual abuse material carries significant legal risks. Law enforcement agencies actively investigate online criminal activity, and while Tor’s anonymity makes tracing individuals more difficult, it’s not impossible. Investigations often involve sophisticated techniques like network analysis, metadata examination, and cooperation between international law enforcement agencies.
Successful prosecutions often hinge on evidence gathered outside the Tor network, such as financial transactions or communication records linked to the user’s real identity. The penalties for such crimes can be severe, ranging from hefty fines to lengthy prison sentences, depending on the jurisdiction and the severity of the offense. The anonymity offered by Tor does not grant immunity from prosecution; it simply increases the difficulty of investigation.
Ethical Considerations Surrounding the Use of Tor for Privacy Protection
The ethical considerations surrounding Tor’s use for privacy protection are nuanced. While many individuals utilize Tor to protect their privacy from government surveillance, corporate tracking, or online harassment, the same anonymity can be exploited for malicious purposes. The potential for misuse raises questions about the responsibility of both Tor developers and users. Developers must strive to balance anonymity with security, implementing measures to mitigate the risk of misuse.
Users, in turn, have a moral obligation to use Tor responsibly, refraining from activities that could harm others. The ethical dilemma lies in weighing the benefits of privacy protection against the potential for harm caused by anonymity. For instance, whistleblowers might use Tor to expose wrongdoing, while others might use it to engage in illegal activities.
Comparison of Tor Use for Legitimate and Illegitimate Purposes
The core functionality of Tor remains the same regardless of its intended use: providing anonymity and encryption. The difference lies solely in the user’s intent and actions. Legitimate uses include protecting journalists’ sources, enabling dissidents in oppressive regimes to communicate safely, and safeguarding the privacy of individuals facing online harassment. Illegitimate uses, conversely, include facilitating illegal marketplaces, enabling cybercrime, and hiding evidence of criminal activity.
The key distinction lies not in the technology itself but in the ethical and legal framework within which it’s employed. The same tools can be used for good or ill, highlighting the crucial role of individual responsibility and the importance of ethical considerations in technology use.
Tor’s Role in Protecting Whistleblowers and Journalists
Tor has become a vital tool for whistleblowers and journalists seeking to protect their sources and publish sensitive information without fear of reprisal. The anonymity it provides allows them to communicate securely with sources, share documents confidentially, and publish sensitive information without revealing their identity or location. This protection is crucial in situations where revealing one’s identity could lead to arrest, harassment, or even violence.
Examples include Edward Snowden’s use of Tor to leak classified information and various journalists using it to communicate with sources in conflict zones or under authoritarian regimes. However, it’s important to note that Tor doesn’t offer absolute anonymity; sophisticated surveillance techniques can still potentially compromise user privacy. Nevertheless, it significantly enhances the security and privacy of whistleblowers and journalists, enabling them to perform their crucial role in holding power accountable.
Tor Browser User Interface

The Tor Browser’s user interface is designed with simplicity and security in mind. It aims to provide a familiar browsing experience while prioritizing user privacy and anonymity. While it shares similarities with other browsers, key differences exist to enhance security features. The interface is intentionally minimalistic, avoiding unnecessary bells and whistles that could compromise security.The Tor Browser interface closely resembles Firefox, its foundation, but with crucial security enhancements built-in.
The main window displays the familiar address bar, tabs, and navigation buttons. However, features like extensions and add-ons are heavily restricted to maintain the browser’s security profile. The NoScript feature is enabled by default, blocking JavaScript execution unless explicitly allowed on specific websites, mitigating potential security risks. A prominent “Connect” button is present to initiate the Tor connection, clearly indicating the status of the anonymizing network.
Tor Browser UI Key Features
The Tor Browser’s user interface incorporates several key features designed to enhance security and user privacy. These features are distinct from those found in mainstream browsers and contribute to the browser’s overall security posture. The most important features include a built-in NoScript feature, a hardened Firefox configuration, and the prominent “Connect” button. Additionally, the interface prominently displays the Tor network status, offering users visual confirmation of their anonymized connection.
Comparison of Tor Browser UI with Other Common Browsers
| Feature | Tor Browser | Chrome | Firefox |
|---|---|---|---|
| Default Appearance | Minimalist, resembling Firefox | Modern, customizable | Customizable, various themes available |
| Extension Support | Highly restricted | Extensive support | Extensive support |
| Security Features | NoScript enabled by default, hardened configuration | Built-in security features, extensions available | Built-in security features, extensions available |
| Privacy Settings | Emphasis on privacy; strict settings | Customizable privacy settings | Customizable privacy settings |
Navigating and Using Tor Browser Settings
Accessing Tor Browser settings is straightforward. Click on the three horizontal lines (hamburger menu) typically located in the upper right corner of the browser window. Select “Settings” from the dropdown menu. The settings menu is categorized for easy navigation, allowing users to manage their privacy preferences, network settings, and security configurations. Options include managing security levels, customizing privacy settings, and selecting language preferences.
The “Advanced” settings provide more granular control over various aspects of the browser.
Tips and Tricks for Optimizing Tor Browser Performance
Several strategies can improve Tor Browser performance. Disabling unnecessary browser extensions, which are heavily restricted anyway, is a key step. Closing unused tabs frees up system resources. Keeping the browser updated ensures access to the latest performance and security enhancements. Regularly clearing the browser cache and cookies can also contribute to improved speed and efficiency.
Using a solid-state drive (SSD) instead of a traditional hard drive (HDD) significantly enhances overall system performance, including browser speed. Finally, ensuring sufficient RAM and processor power on your device will help improve browser responsiveness.
Tor Browser Extensions and Add-ons
Extending Tor Browser’s functionality with extensions and add-ons can enhance your browsing experience, but it’s crucial to understand the potential security implications. While some add-ons offer valuable features, others might compromise your anonymity or introduce vulnerabilities. Careful selection and understanding are key to safe and effective use.Adding extensions to Tor Browser is different than in other browsers because of the heightened security focus.
Tor prioritizes user privacy and anonymity, so extensions undergo more scrutiny before they’re allowed. This means fewer extensions are available compared to Chrome or Firefox, but those that are available are generally vetted more carefully.
Popular Tor Browser Extensions and Add-ons
Several extensions enhance Tor’s capabilities. Notably, HTTPS Everywhere, a popular extension across many browsers, enforces HTTPS connections whenever possible, increasing security and privacy by encrypting communications between your browser and websites. Another example is NoScript, which blocks JavaScript, Flash, and other plugins unless explicitly allowed. This significantly reduces the attack surface, preventing many malicious scripts from executing.
While these are not exclusive to Tor, their functionality is especially relevant within the Tor ecosystem.
Security-Enhancing Add-ons for Tor, Tor browser
It’s vital to prioritize security when selecting extensions for Tor. Extensions that improve security usually focus on enhancing encryption, blocking trackers, and improving overall privacy. A hypothetical example would be an extension that automatically detects and blocks known fingerprinting techniques, thus further masking your online identity. Another could be an add-on that regularly checks for and updates your browser’s security settings, ensuring you are using the latest protections.
However, remember that no single extension guarantees complete anonymity; a layered approach to security is always best.
Installing and Managing Extensions in Tor
Installing extensions in Tor Browser is relatively straightforward. The process typically involves navigating to the Tor Browser’s settings menu, locating the “Extensions” section, and then selecting “Get Add-ons”. From there, you can browse the available extensions, read descriptions, and install those that meet your needs. Managing extensions involves enabling or disabling them, or removing them entirely through the same settings menu.
This simple process ensures that users can easily customize their Tor Browser experience while maintaining control over their privacy settings.
Security Implications of Using Different Extensions
The security implications of using extensions vary greatly. While some extensions, like HTTPS Everywhere, enhance security, others might introduce vulnerabilities if not properly vetted or maintained. For example, a poorly coded or malicious extension could expose your IP address or compromise your anonymity. Therefore, only installing extensions from trusted sources and carefully reviewing their permissions is crucial.
Prioritizing extensions with open-source code, allowing for community scrutiny and verification, is a good practice. Ultimately, the risk-benefit analysis for each extension must be carefully considered. Remember, the more extensions you use, the larger your attack surface becomes.
Troubleshooting Common Tor Issues: Tor Browser
Let’s be real, Tor isn’t always a smooth ride. Sometimes it can be frustratingly slow, or you might run into unexpected errors. This section covers some of the most common problems Tor users face and offers practical solutions to get you back online and browsing privately. Think of it as your go-to guide for when things go sideways.
Connectivity Issues
Connectivity problems are among the most frequent complaints from Tor users. These issues can range from a complete inability to connect to the Tor network to intermittent slowdowns. Several factors can contribute to these problems, including network configuration, firewall settings, and even ISP interference.
- Check your network connection: Before troubleshooting Tor, ensure your computer is properly connected to the internet. Try accessing a website outside of Tor to confirm basic internet connectivity.
- Examine your firewall or antivirus software: Firewalls and antivirus programs can sometimes block Tor’s connections. Temporarily disable these programs to see if that resolves the issue. If it does, configure your security software to allow Tor Browser.
- Verify your proxy settings: If you’re using a proxy server, ensure it’s correctly configured and not interfering with Tor’s functionality. Tor should generally not be used with other proxy servers.
- Restart your computer and router: A simple restart can often resolve temporary network glitches.
- Check your Tor network status: Sometimes, problems stem from the Tor network itself. Visit the Tor Project website to check for any reported outages or issues.
Slow Browsing Speeds
Tor is inherently slower than regular browsing due to the multiple layers of encryption and routing. However, excessively slow speeds can indicate a problem.
- Close unnecessary applications: Other programs competing for bandwidth can significantly impact Tor’s performance.
- Check your internet connection speed: A slow internet connection will naturally slow down Tor browsing. Consider upgrading your internet plan if necessary.
- Try a different bridge: If you’re using a bridge, try switching to a different one. Bridges are alternative entry points to the Tor network and can sometimes offer better performance.
- Clear your cache and cookies: A cluttered cache and cookies can slow down any browser, including Tor.
- Disable or uninstall browser extensions: Extensions can consume resources and affect Tor’s speed. Disable or uninstall any unnecessary extensions.
Troubleshooting Tor Browser Errors and Malfunctions
Encountering error messages within Tor Browser can be unnerving, but often, the solutions are straightforward.
- Check the error message: Carefully read any error messages that appear. They often provide clues about the problem’s source.
- Restart Tor Browser: A simple restart can often resolve temporary glitches.
- Update Tor Browser: Outdated versions can contain bugs and security vulnerabilities. Regularly check for and install updates.
- Reinstall Tor Browser: If problems persist after trying other troubleshooting steps, reinstalling Tor Browser can be a helpful solution. Ensure you download it from the official Tor Project website.
- Consult the Tor Project support resources: The Tor Project website offers extensive documentation and troubleshooting guides. Their forums and support channels are also excellent resources for finding solutions to specific problems.
Comparison with Other Privacy Tools
Choosing the right privacy tool depends heavily on your specific needs and threat model. While Tor Browser, VPNs, and other anonymity tools all aim to enhance online privacy, they operate differently and offer varying levels of protection against different types of surveillance. Understanding these differences is crucial for making an informed decision.Tor Browser and VPNs are often compared, but they are not interchangeable.
They offer different strengths and weaknesses. Thinking of them as complementary tools rather than competitors can be helpful in understanding their unique roles.
Tor Browser versus VPNs
Tor Browser and VPNs each provide a layer of anonymity, but they achieve this through different mechanisms. VPNs mask your IP address by routing your internet traffic through a remote server, making it appear as though you’re browsing from the VPN server’s location. Tor, on the other hand, routes your traffic through a series of volunteer-operated relays, obscuring your origin and destination.
This multi-layered approach makes it significantly harder to track your online activity. However, VPNs generally offer faster speeds because they involve a single hop, while Tor’s multi-hop process can slow down your browsing. A VPN might be sufficient for general privacy concerns like hiding your location from your ISP, but for those needing stronger protection against sophisticated adversaries, Tor’s layered approach offers a significant advantage.
A combination of both – using a VPN to mask your IP address
before* connecting to the Tor network – can provide even greater anonymity, though this also adds complexity.
Tor and Other Anonymity Tools
Beyond VPNs, other anonymity tools exist, each with its own set of strengths and weaknesses. For example, privacy-focused search engines like DuckDuckGo prioritize protecting your search queries from tracking, but they don’t encrypt your entire browsing activity like Tor. Similarly, encrypted messaging apps like Signal secure your communications, but don’t necessarily protect your browsing activity. These tools can be used in conjunction with Tor for a more comprehensive approach to online privacy, depending on your specific needs.
Consider the privacy-focused browser Brave, which blocks trackers by default but doesn’t offer the same level of anonymity as Tor. The choice often comes down to balancing convenience and security; more secure solutions frequently come with trade-offs in speed and usability.
Comparison of Privacy Solutions
The following table compares the features and benefits of several popular privacy solutions. Note that the effectiveness of each tool depends heavily on its proper configuration and use.
| Tool | Privacy Level | Speed | Ease of Use |
|---|---|---|---|
| Tor Browser | High (multi-layered encryption and anonymity) | Low (due to multiple hops) | Moderate (requires understanding of its functionality) |
| VPN | Moderate (masks IP address) | High (single hop) | High (generally user-friendly) |
| DuckDuckGo | Moderate (protects search queries) | High | High |
| Signal | High (end-to-end encryption for messaging) | High | High |
| Brave Browser | Moderate (blocks trackers) | High | High |
Tor Browser’s Role in Censorship Circumvention
Tor’s anonymity features make it a powerful tool for circumventing internet censorship and restrictions imposed by governments or organizations. By routing traffic through multiple relays, Tor obscures the user’s origin and destination, making it difficult for censors to block access to specific websites or content. This is particularly relevant in countries with strict online controls where access to information is heavily restricted.Tor achieves censorship circumvention by employing a layered approach to network communication.
Instead of sending data directly to its destination, Tor bounces the data through a series of volunteer-operated servers known as “nodes” or “relays.” Each relay only knows the address of the relay before it and the one after it, effectively masking the user’s IP address and location. This makes it challenging for censors to identify and block individual users or pinpoint the origin of the request.
The more relays involved, the more difficult it becomes to trace the communication back to the user.
Tor’s Use in Countries with Strict Online Controls
The implications of Tor’s use in countries with strict online controls are significant. In these regions, governments often employ sophisticated censorship techniques, including deep packet inspection and URL filtering, to limit access to information deemed undesirable. Tor provides a lifeline for citizens seeking access to news, social media, and other online resources that might be blocked. Journalists, activists, and human rights organizations rely on Tor to communicate securely and share information without fear of surveillance or reprisal.
However, it’s crucial to acknowledge that Tor is not foolproof, and sophisticated censorship mechanisms can still detect and block Tor traffic, albeit with increased difficulty. The effectiveness of Tor depends on factors such as the sophistication of the censorship technology employed and the number of available Tor relays.
Challenges Faced by Tor Users in Circumventing Censorship
Despite its effectiveness, Tor users often face challenges in circumventing censorship. Governments and organizations actively work to block Tor traffic, using various techniques such as DNS poisoning, deep packet inspection, and the blocking of Tor exit nodes. These efforts can make accessing the open internet through Tor difficult, resulting in slow speeds, connection failures, and the inability to access certain websites.
Furthermore, Tor’s reliance on volunteer-operated relays means that the network’s stability and performance can fluctuate. The number and location of relays are critical; limited availability in certain regions can hinder Tor’s effectiveness. Finally, users must be aware of the security implications of using Tor, including the risk of compromised relays and the potential for traffic analysis.
Tor Browser’s anonymity features are awesome, but sometimes you accidentally delete crucial files while using it. If that happens, don’t freak; you can use a program like the easeus data recovery wizard to potentially get your stuff back. Then, you can get back to browsing privately with Tor, knowing your data is safe(r).
Examples of Tor’s Use in Overcoming Censorship
Tor has played a crucial role in enabling communication and access to information in numerous countries with restrictive internet policies. During the Arab Spring uprisings, for example, activists and journalists used Tor to share information and organize protests despite government efforts to block access to social media and news websites. Similarly, Tor has been used by dissidents in authoritarian regimes to communicate with the outside world and expose human rights abuses.
In countries with strict online controls, Tor has facilitated access to educational resources, medical information, and independent news sources that are otherwise unavailable. While specific examples often remain undisclosed for security reasons, the impact of Tor in overcoming censorship is undeniable and continues to be significant.
Future Developments and Trends

Predicting the future of Tor is a complex task, given the constantly evolving landscape of online surveillance and anonymity technologies. However, by examining current trends and challenges, we can anticipate some likely developments and their potential impact on the project’s ability to provide secure and private browsing.The future of Tor hinges on its ability to adapt to new threats and leverage emerging technologies.
This involves ongoing improvements to its core architecture, a proactive response to evolving surveillance techniques, and continued community engagement to ensure its long-term viability.
Improved Performance and Usability
Tor’s current performance can be a bottleneck for users, particularly in regions with limited bandwidth. Future developments will likely focus on improving speed and reducing latency. This could involve optimizing the network routing algorithms, exploring alternative consensus mechanisms, and developing more efficient encryption techniques. For example, implementing techniques like QUIC (Quick UDP Internet Connections) could significantly improve connection speeds and reliability, especially on mobile networks.
Furthermore, a streamlined user interface with improved onboarding and help features could increase user adoption and reduce the learning curve associated with using the browser.
Enhanced Security Against Advanced Attacks
As adversarial techniques become more sophisticated, Tor needs to adapt its defenses. This involves ongoing research into new cryptographic primitives and strengthening existing protocols against attacks like traffic analysis and fingerprinting. For instance, exploring post-quantum cryptography to prepare for the advent of quantum computers is a crucial aspect of long-term security. Additionally, improved techniques to detect and mitigate against exit node compromises are essential to maintaining user privacy.
Imagine a scenario where an exit node is compromised; Tor’s developers would need to detect this anomaly quickly and reroute traffic to prevent data leakage.
The Impact of Decentralization and Blockchain Technologies
The increasing interest in decentralized technologies offers both opportunities and challenges for Tor. Blockchain technology could potentially enhance the anonymity of the network by distributing trust and reducing reliance on centralized authorities. However, integrating blockchain into Tor’s architecture would require careful consideration of scalability, security, and the potential for new attack vectors. The challenge lies in balancing the benefits of decentralization with the need for efficient and secure operation.
A hypothetical example might involve using blockchain to create a distributed reputation system for Tor relays, reducing the risk of malicious nodes impacting the network.
Challenges in Maintaining Security and Anonymity
The Tor project faces constant challenges in maintaining security and anonymity. These include the ever-evolving tactics of state-sponsored surveillance, the ongoing arms race between attackers and defenders, and the difficulty of balancing security with usability. Funding remains a persistent challenge, as maintaining a robust and secure network requires significant resources. Additionally, the increasing sophistication of machine learning techniques poses a threat to the anonymity provided by Tor, requiring the development of countermeasures to detect and evade such attacks.
For example, the development of more sophisticated traffic analysis techniques could potentially reveal patterns in Tor traffic, thereby compromising user anonymity.
Predictions for the Future of Tor
Tor’s future depends on its ability to adapt and innovate. We predict that Tor will continue to be a vital tool for activists, journalists, and individuals seeking to protect their online privacy in the face of increasing surveillance. However, its continued success will require ongoing research, development, and community support. It’s likely that Tor will integrate more advanced anonymity techniques, such as improved obfuscation methods and more resilient network architectures.
The integration of new technologies, while posing challenges, also presents opportunities for enhancing security and usability. We also anticipate increased collaboration with other privacy-focused projects and organizations to strengthen the overall ecosystem of online anonymity. The success of Tor, therefore, is intertwined with the broader landscape of privacy technology and the ongoing struggle for online freedom.
End of Discussion
So, there you have it – a deep dive into the world of Tor Browser. While it’s not a magic bullet for complete anonymity, Tor offers a powerful way to enhance your online privacy and security. By understanding its functionality, limitations, and best practices, you can confidently navigate the web with a significantly reduced digital footprint. Remember, responsible and ethical use is key.
Happy browsing (anonymously, of course!).
Query Resolution
Is Tor Browser slow?
Yes, it can be slower than regular browsers because your traffic is routed through multiple servers. The speed depends on server load and your internet connection.
Is Tor Browser legal?
Using Tor itself is legal in most countries. However, using it for illegal activities is not. Tor is a tool; its use is determined by the user.
Can Tor protect me from malware?
Tor enhances your anonymity, but it doesn’t offer complete protection against malware. You still need to practice safe browsing habits and use antivirus software.
Does Tor hide my IP address completely?
Tor masks your IP address, but it doesn’t guarantee complete anonymity. The exit node’s IP address is still visible to the websites you visit.
What are the risks of using Tor?
Risks include slower speeds, potential connection issues, and the possibility of encountering malicious exit nodes. Always use reputable resources and be cautious.