TeamViewer Monitoring & Asset Management empowers businesses to gain complete control over their IT infrastructure, from proactive monitoring to efficient asset management. This comprehensive solution enables organizations to remotely oversee their devices, anticipate potential issues, and streamline asset lifecycle management, ultimately leading to improved operational efficiency and reduced downtime.
Table of Contents
By leveraging TeamViewer’s robust features, organizations can gain real-time insights into the health and performance of their systems, proactively identify and resolve issues before they impact business operations. Furthermore, TeamViewer’s asset management capabilities provide a centralized platform for inventorying, tracking, and managing all IT assets, ensuring optimal utilization and compliance with industry regulations.
Introduction to TeamViewer Monitoring & Asset Management
TeamViewer Monitoring & Asset Management is a powerful suite of tools that allows you to remotely monitor and manage your IT infrastructure and assets, regardless of their physical location. It provides a comprehensive solution for organizations of all sizes, enabling them to improve efficiency, reduce downtime, and enhance security.
Remote Monitoring and Management
Remote monitoring and management (RMM) is a technology that allows IT professionals to remotely monitor and manage computer systems and networks. It enables them to access and control devices, perform troubleshooting, install software, and implement security updates from a central location. RMM solutions like TeamViewer Monitoring & Asset Management provide a centralized platform for managing all aspects of an IT environment, making it easier to identify and resolve issues before they impact users.
Benefits of TeamViewer Monitoring & Asset Management
TeamViewer Monitoring & Asset Management offers several benefits for organizations, including:
- Improved Efficiency: RMM tools automate routine tasks such as software updates, patch management, and system backups, freeing up IT staff to focus on more strategic initiatives.
- Reduced Downtime: By proactively monitoring systems and identifying potential issues before they become critical, RMM solutions can minimize downtime and ensure business continuity.
- Enhanced Security: RMM tools help organizations enforce security policies, manage user access, and implement real-time threat detection and response mechanisms, reducing the risk of cyberattacks.
- Cost Savings: RMM solutions can reduce the need for on-site IT staff, lower travel expenses, and optimize hardware and software usage, leading to significant cost savings.
Examples of TeamViewer Monitoring & Asset Management Use Cases
TeamViewer Monitoring & Asset Management can be used for a wide range of monitoring and asset management tasks, including:
- System Monitoring: Monitor key system metrics such as CPU usage, memory utilization, disk space, and network traffic to identify potential performance bottlenecks and proactively address issues.
- Software and Patch Management: Automate software updates and patch deployment across all devices, ensuring all systems are up-to-date and secure.
- Security Management: Monitor security events, manage user access, and implement security policies to protect against unauthorized access and cyber threats.
- Asset Inventory: Track and manage all IT assets, including hardware, software, and licenses, to ensure accurate inventory and optimize resource utilization.
- Remote Support: Provide remote technical support to end-users, troubleshoot issues, and resolve problems quickly and efficiently.
TeamViewer Monitoring Features
TeamViewer Monitoring offers a comprehensive suite of features designed to provide real-time insights into the health and performance of your devices and applications. This proactive approach enables you to identify and resolve issues before they impact your business operations, ensuring optimal system uptime and productivity.
Real-Time Device Monitoring
Real-time device monitoring provides continuous visibility into the status of your devices, enabling you to stay informed about their current state and identify potential issues proactively.
- System Resource Utilization: Track key performance indicators (KPIs) such as CPU usage, memory consumption, disk space, and network bandwidth. This information helps you understand how your devices are performing and identify potential bottlenecks. For example, if you notice a sudden spike in CPU usage, you can investigate the cause and take corrective action before it affects other processes.
- Service Status: Monitor the status of critical services and applications running on your devices, ensuring they are operational and functioning as expected. This includes checking for service failures, restarts, or unexpected behavior. For example, if a database service crashes, you’ll receive immediate alerts, allowing you to restore the service quickly and minimize downtime.
- Event Logging: Capture and analyze system events, such as errors, warnings, and informational messages. This information provides valuable insights into device behavior and helps you diagnose problems more effectively. For example, by examining the system logs, you can identify recurring errors that indicate a potential hardware or software issue.
System Health Checks
System health checks are designed to proactively identify and resolve potential issues before they impact your operations.
- Automated Health Scans: Regularly perform automated scans to assess the overall health of your devices. These scans check for common problems, such as outdated software, missing security patches, or disk space issues. By addressing these issues early, you can prevent them from escalating into major problems.
- Performance Optimization: Identify areas where your devices can be optimized for better performance. This includes recommendations for software updates, hardware upgrades, or configuration changes that can improve efficiency and responsiveness. For example, by optimizing your server configuration, you can reduce resource consumption and improve application performance.
- Security Monitoring: Detect potential security threats, such as malware infections, unauthorized access attempts, or network vulnerabilities. By implementing appropriate security measures, you can protect your devices and data from malicious attacks. For example, you can configure alerts for suspicious network activity or unauthorized software installations.
Performance Tracking
Performance tracking provides valuable insights into how your devices and applications are performing over time.
- Historical Data Analysis: Analyze historical data to identify trends and patterns in device performance. This helps you understand how your systems are evolving and identify potential areas for improvement. For example, by analyzing historical CPU usage data, you can identify periods of high demand and optimize your resource allocation accordingly.
- Performance Benchmarks: Compare your device performance against industry benchmarks to assess their overall health and identify areas where improvement is possible. This allows you to set realistic performance goals and track your progress over time. For example, you can compare your server performance against industry benchmarks to ensure that it meets the requirements of your applications.
- Customizable Dashboards: Create customized dashboards to visualize key performance indicators (KPIs) and track the performance of your devices and applications. This allows you to monitor your systems in real-time and identify any potential issues quickly. For example, you can create a dashboard that displays CPU usage, memory consumption, and network bandwidth for all your servers.
Asset Management with TeamViewer
TeamViewer is not just a remote access tool; it can be a powerful asset management solution. Its features go beyond simple remote control and provide a comprehensive platform for inventorying, managing, and maintaining your IT assets, including hardware and software.
Asset Management Features
TeamViewer’s asset management capabilities are designed to streamline your IT processes and enhance visibility across your entire IT infrastructure.
- Inventory Management: TeamViewer allows you to create a centralized inventory of all your IT assets, including hardware and software. You can automatically discover devices on your network, collect detailed hardware information, and track software licenses. This provides a comprehensive overview of your IT assets, making it easier to manage and optimize your resources.
- Remote Access: TeamViewer’s core functionality, remote access, is also crucial for asset management. It allows you to access and manage devices remotely, perform troubleshooting, install software updates, and perform other tasks without physically being present at the device. This significantly reduces downtime and improves efficiency.
- Software Deployment: TeamViewer’s software deployment capabilities allow you to remotely install, update, and manage software on multiple devices simultaneously. This eliminates the need for manual installations and ensures that all devices have the latest software versions, reducing security risks and improving performance.
- Patch Management: TeamViewer integrates with your existing patch management solutions, allowing you to automatically deploy security patches and updates to your devices. This helps ensure that your devices are protected from the latest vulnerabilities and keeps your IT infrastructure secure.
Streamlining Asset Management Tasks
Here’s a table illustrating how TeamViewer can streamline common asset management tasks:
| Task | TeamViewer Feature | Benefits |
|—|—|—|
| Inventorying devices | Device discovery, hardware information collection | Accurate and up-to-date inventory, reduced manual effort |
| Tracking software licenses | Software license management | Improved compliance, reduced costs, and optimized software usage |
| Deploying software updates | Software deployment feature | Reduced downtime, improved security, and enhanced user experience |
| Managing security patches | Patch management integration | Enhanced security, minimized vulnerabilities, and streamlined patch deployment |
| Troubleshooting issues | Remote access and control | Faster resolution of issues, reduced downtime, and improved user productivity |
Security Considerations
Using TeamViewer for monitoring and asset management introduces security considerations that need careful attention. It’s essential to implement robust security measures to protect sensitive data and ensure the integrity of your systems. This section will explore best practices for securing TeamViewer deployments, including user authentication, access control, and encryption. We’ll also discuss common security vulnerabilities and mitigation strategies.
User Authentication and Access Control
User authentication and access control are crucial for preventing unauthorized access to your systems. TeamViewer offers various authentication methods, including two-factor authentication (2FA), to enhance security. Implementing strong passwords and limiting user privileges can further strengthen your security posture.
- Two-factor Authentication (2FA): Enabling 2FA adds an extra layer of security by requiring users to provide a second factor, such as a code from a mobile app or a physical security key, in addition to their password. This significantly reduces the risk of unauthorized access, even if an attacker compromises a user’s password.
- Strong Passwords: Encourage users to create strong passwords that include a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable passwords like names, birthdays, or common phrases.
- Privilege Management: Grant users only the permissions they need to perform their tasks. Avoid giving all users administrator privileges. Implement role-based access control (RBAC) to ensure that users can only access the resources they are authorized to use.
Encryption
Data encryption is essential for protecting sensitive information during transmission and storage. TeamViewer uses industry-standard encryption protocols to secure communication between devices. It’s important to understand the encryption methods used and ensure they are up-to-date and compliant with security best practices.
- End-to-End Encryption: TeamViewer utilizes end-to-end encryption, which means that data is encrypted on the sending device and only decrypted on the receiving device. This prevents unauthorized parties from intercepting and decrypting data during transmission.
- Encryption Algorithms: TeamViewer uses robust encryption algorithms like AES-256, which is widely considered to be a secure and reliable encryption method.
- Encryption Keys: The encryption keys used by TeamViewer are generated and managed securely. They are not stored in plain text, further enhancing the security of data transmission.
Security Vulnerabilities and Mitigation, Teamviewer monitoring & asset management
While TeamViewer offers strong security features, it’s important to be aware of potential vulnerabilities and implement mitigation strategies. Regularly updating TeamViewer to the latest version is crucial for patching security holes and staying protected.
- Unpatched Vulnerabilities: Outdated versions of TeamViewer may contain known security vulnerabilities that attackers can exploit. Regularly updating to the latest version ensures that you have the latest security patches and are protected against known vulnerabilities.
- Phishing Attacks: Attackers may attempt to trick users into providing their login credentials through phishing emails or websites. It’s important to be cautious about suspicious emails and links, and to never share your login credentials with unknown parties.
- Brute-Force Attacks: Attackers may try to guess user passwords through automated brute-force attacks. Implementing strong passwords and enabling 2FA can effectively mitigate this threat.
- Malware Infections: Malicious software can compromise your devices and gain access to your TeamViewer account. Install and maintain reputable antivirus software to protect your systems from malware infections.
Use Cases and Examples
TeamViewer Monitoring and Asset Management offers a versatile solution for managing and monitoring diverse IT environments. From small businesses to large enterprises, TeamViewer provides a comprehensive approach to streamlining operations and ensuring optimal performance.
Real-World Examples Across Industries
Here are some real-world examples of how TeamViewer is used for monitoring and asset management in various industries:
- Healthcare: Hospitals and clinics use TeamViewer to monitor critical medical equipment, ensuring patient safety and operational efficiency. For example, they can remotely monitor vital signs, temperature control systems, and other critical equipment. They can also manage software licenses and updates for medical imaging software and other essential applications. This ensures that all medical devices and software are running smoothly and securely.
- Manufacturing: Manufacturing companies leverage TeamViewer to monitor production lines, identify potential issues, and manage industrial assets. For example, they can monitor the performance of machines, track inventory levels, and ensure that production processes are running smoothly. They can also use TeamViewer to manage software licenses and updates for industrial control systems, ensuring that all systems are up-to-date and secure.
- Education: Educational institutions utilize TeamViewer to monitor computer labs, troubleshoot technical issues, and manage software licenses for students and faculty. They can also use TeamViewer to provide remote support to students and faculty, ensuring that everyone has access to the necessary resources. This allows educational institutions to provide efficient and effective IT support to students and faculty.
- Finance: Financial institutions rely on TeamViewer to monitor and manage critical infrastructure, ensuring the security and stability of their operations. They can remotely monitor servers, network devices, and other critical systems. They can also use TeamViewer to manage software licenses and updates for financial applications, ensuring that all systems are up-to-date and secure. This helps financial institutions comply with regulatory requirements and maintain a secure and reliable IT environment.
Monitoring a Critical Server Infrastructure
Imagine a scenario where a company has a critical server infrastructure that powers their online services. Using TeamViewer, the IT team can:
- Monitor server performance: Track CPU usage, memory consumption, disk space, and network traffic to identify potential bottlenecks and ensure optimal performance.
- Receive alerts: Set up alerts for critical events, such as high CPU usage, low disk space, or network connectivity issues. This enables proactive problem-solving and prevents potential downtime.
- Remotely access and manage servers: Troubleshoot issues, install updates, and perform other administrative tasks remotely. This minimizes downtime and ensures that the server infrastructure remains operational.
- Manage software licenses: Track and manage software licenses for operating systems, applications, and other software components on the servers. This ensures compliance with licensing agreements and prevents potential legal issues.
Managing Software Licenses and Updates
TeamViewer simplifies the process of managing software licenses and updates across a network.
- Centralized software license management: Track and manage all software licenses across the network, ensuring compliance with licensing agreements and preventing potential legal issues.
- Automated software updates: Schedule and deploy software updates to all devices on the network, ensuring that all systems are up-to-date and secure. This reduces the risk of security vulnerabilities and ensures that all devices are running the latest versions of software.
- Software inventory management: Track all software installed on network devices, providing a comprehensive inventory of software assets. This helps IT teams understand the software landscape and identify potential vulnerabilities or outdated software.
Integration and Automation
TeamViewer’s strength lies not only in its remote access capabilities but also in its ability to seamlessly integrate with other IT management tools and systems, enabling powerful automation of routine tasks. This integration and automation empower organizations to streamline their IT operations, improve efficiency, and enhance overall productivity.
Integration with Other Tools
TeamViewer’s integration capabilities extend its reach, allowing it to work in harmony with existing IT infrastructure. This integration enables a comprehensive view of the IT landscape, fostering a cohesive and efficient management approach.
- IT Service Management (ITSM) Tools: TeamViewer integrates with leading ITSM platforms like ServiceNow, Jira, and Zendesk. This integration allows for seamless ticket creation and management within TeamViewer, streamlining incident resolution and improving communication between IT support and users.
- Monitoring and Management Platforms: TeamViewer can be integrated with monitoring tools like Nagios, PRTG, and SolarWinds, enabling centralized monitoring of devices and systems. This integration provides a holistic view of system health, allowing for proactive issue detection and resolution.
- Active Directory (AD) and LDAP: TeamViewer integrates with AD and LDAP, allowing for centralized user management and authentication. This integration simplifies user provisioning and access control, ensuring secure and efficient access to devices and applications.
Automation Features
TeamViewer offers a suite of automation features that streamline routine monitoring and asset management tasks, freeing up valuable time for IT professionals to focus on strategic initiatives.
- Automated Device Discovery: TeamViewer’s automated device discovery feature automatically identifies and adds new devices to the inventory, reducing manual effort and ensuring a comprehensive asset inventory.
- Scheduled Tasks: TeamViewer allows scheduling of tasks like software updates, system maintenance, and script execution. This automated approach ensures timely updates and maintenance, minimizing downtime and improving system stability.
- Remote Script Execution: TeamViewer enables the remote execution of scripts and commands, allowing for automated configuration changes, software deployments, and system troubleshooting. This capability significantly reduces the need for manual intervention, improving efficiency and consistency.
Examples of Automation
TeamViewer’s automation features can be leveraged to streamline various IT processes, including:
- Software Deployment: TeamViewer can be used to automatically deploy software updates and applications to multiple devices simultaneously, reducing manual effort and ensuring consistent deployments across the organization.
- System Updates: TeamViewer can automate the process of updating operating systems and security patches on managed devices, ensuring systems are up-to-date and secure. This automation eliminates the need for manual updates, reducing the risk of security vulnerabilities and system instability.
- Remote Configuration: TeamViewer can be used to remotely configure devices and applications, enabling standardized settings and configurations across the organization. This automation simplifies configuration management and ensures consistency across devices and systems.
Benefits and Challenges
TeamViewer offers a compelling alternative to traditional monitoring and asset management methods, bringing several advantages to the table. However, like any technology, it also presents potential challenges that need to be addressed for successful implementation. This section explores the benefits and challenges associated with using TeamViewer for these purposes.
Benefits of Using TeamViewer
TeamViewer provides a range of benefits over traditional methods for monitoring and asset management, making it a popular choice for businesses of all sizes.
- Remote Access and Control: TeamViewer allows users to access and control remote devices securely from anywhere with an internet connection. This eliminates the need for physical presence, saving time and resources, especially when dealing with geographically dispersed assets.
- Real-Time Monitoring: TeamViewer provides real-time monitoring capabilities, enabling users to track key metrics and performance indicators of their assets. This real-time data allows for proactive identification and resolution of issues before they escalate, minimizing downtime and potential disruptions.
- Simplified Asset Management: TeamViewer simplifies asset management by providing a centralized platform for tracking and managing all devices and software. This eliminates the need for multiple tools and databases, streamlining processes and reducing administrative overhead.
- Cost-Effectiveness: Compared to traditional methods, TeamViewer offers a cost-effective solution, eliminating the need for expensive hardware and software investments. Its subscription-based model allows businesses to scale their monitoring and asset management capabilities based on their specific requirements.
- Enhanced Collaboration: TeamViewer facilitates collaboration by allowing multiple users to access and manage assets simultaneously. This enables efficient problem-solving and knowledge sharing, leading to faster resolution times and improved team performance.
Challenges of Using TeamViewer
While TeamViewer offers numerous benefits, it also presents some challenges that organizations need to consider.
- Network Latency: Network latency can impact the performance of TeamViewer, especially when accessing remote devices with poor internet connectivity. This can lead to delays in data transmission and slow response times, hindering real-time monitoring and remote control.
- Security Risks: Security is a critical concern when using remote access software. TeamViewer employs robust security measures, but organizations must implement best practices to mitigate potential risks. These practices include using strong passwords, enabling two-factor authentication, and regularly updating software to patch vulnerabilities.
- User Adoption: Successful implementation of TeamViewer depends on user adoption. Organizations need to provide adequate training and support to ensure users are comfortable and proficient in using the software. This involves clear communication, hands-on training, and ongoing support to address any issues or concerns.
Overcoming Challenges
Organizations can overcome the challenges associated with using TeamViewer by adopting a proactive approach.
- Optimize Network Connectivity: To minimize network latency, ensure reliable internet connectivity for both the remote device and the user’s device. Consider using a VPN or dedicated network connection for optimal performance.
- Implement Strong Security Measures: Prioritize security by using strong passwords, enabling two-factor authentication, and regularly updating software to patch vulnerabilities. Encourage users to report any suspicious activity immediately.
- Provide Comprehensive Training and Support: Invest in comprehensive user training to familiarize users with TeamViewer’s features and functionality. Offer ongoing support to address any questions or issues users may encounter.
Future Trends
The landscape of remote monitoring and asset management is rapidly evolving, driven by advancements in technology and the growing demand for efficient and secure IT solutions. Emerging trends like artificial intelligence (AI) and machine learning (ML) are poised to revolutionize how organizations manage their IT infrastructure and assets.
The Rise of AI and ML
AI and ML are playing a crucial role in transforming remote monitoring and asset management. By analyzing vast amounts of data, these technologies can identify patterns, predict potential issues, and automate tasks that were previously manual.
- Predictive Maintenance: AI-powered predictive maintenance models can analyze sensor data from devices to predict potential failures before they occur, enabling proactive maintenance and minimizing downtime. For example, a company using TeamViewer could integrate AI models that analyze data from servers to predict hard drive failures, allowing for timely replacements and preventing data loss.
- Automated Anomaly Detection: ML algorithms can identify anomalies in system performance, network traffic, or device behavior, alerting IT teams to potential security threats or performance issues. This can help organizations quickly respond to incidents and mitigate potential risks.
- Intelligent Asset Management: AI-powered asset management systems can track and manage assets more efficiently, automating tasks like inventory management, software updates, and license compliance. This can free up IT teams to focus on more strategic initiatives.
TeamViewer’s Evolution
TeamViewer is actively embracing these trends to enhance its remote monitoring and asset management capabilities. The company is investing in AI and ML technologies to improve its platform’s ability to analyze data, automate tasks, and provide actionable insights.
- AI-powered Insights: TeamViewer is developing AI-powered features that can analyze data from monitored devices and provide insights into system performance, potential issues, and security threats. This will help IT teams make more informed decisions and proactively address problems.
- Automated Remediation: TeamViewer is exploring the use of AI and ML to automate certain remediation tasks, such as patching vulnerabilities or restarting services. This will further streamline IT operations and reduce the burden on IT teams.
- Enhanced Security: AI and ML can help improve the security of TeamViewer’s platform by detecting and preventing malicious activities, such as unauthorized access or data breaches. This will enhance the overall security posture of organizations using TeamViewer.
The Future of TeamViewer in IT Management
As AI and ML continue to advance, TeamViewer is expected to play an increasingly important role in IT management. The platform’s ability to provide comprehensive remote monitoring, asset management, and AI-powered insights will make it an indispensable tool for organizations seeking to optimize their IT operations and enhance their security posture.
- Proactive and Predictive IT Management: TeamViewer will evolve into a platform that enables proactive and predictive IT management, allowing organizations to anticipate and address issues before they impact operations. This will result in improved system uptime, reduced downtime, and lower operational costs.
- Enhanced Security and Compliance: AI-powered security features will make TeamViewer a more secure platform, helping organizations meet evolving compliance requirements and protect their sensitive data.
- Increased Automation and Efficiency: TeamViewer will continue to automate tasks, freeing up IT teams to focus on more strategic initiatives. This will lead to increased efficiency and productivity within IT departments.
Best Practices for TeamViewer Monitoring & Asset Management
Effective utilization of TeamViewer for monitoring and asset management requires adherence to specific best practices. These practices ensure optimal performance, security, and efficiency in managing your IT infrastructure.
Security Best Practices
- Enable Two-Factor Authentication: This adds an extra layer of security by requiring users to enter a code from their mobile device in addition to their password when logging in. This makes it much harder for unauthorized individuals to access your systems.
- Use Strong Passwords: Encourage users to create strong passwords that are at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
- Regularly Update TeamViewer: Keeping TeamViewer up-to-date is crucial for security. Updates often include patches that address vulnerabilities, making your system more resistant to attacks.
- Restrict Access: Limit access to specific users or groups based on their roles and responsibilities. This helps prevent unauthorized access to sensitive data and systems.
- Use Dedicated Accounts: Create separate TeamViewer accounts for monitoring and asset management tasks. This allows you to track activity and identify potential security breaches more easily.
Monitoring Best Practices
- Define Clear Monitoring Objectives: Before setting up monitoring, clearly define what you want to track. This could include system performance, network usage, or application availability.
- Establish Baselines: Collect data on your systems’ normal behavior to establish a baseline. This helps you identify anomalies and potential problems more effectively.
- Use Alerts: Configure alerts to notify you of critical events, such as system failures, network outages, or security breaches. This allows you to respond quickly to problems before they escalate.
- Regularly Review Monitoring Data: Analyze the data collected by TeamViewer’s monitoring tools to identify trends and potential issues. This proactive approach helps prevent problems from occurring in the first place.
- Integrate with Other Tools: Integrate TeamViewer’s monitoring capabilities with other tools in your IT infrastructure. This provides a more comprehensive view of your systems and allows you to automate tasks.
Asset Management Best Practices
- Create a Centralized Inventory: Use TeamViewer’s asset management features to create a comprehensive inventory of all your devices, software, and other IT assets.
- Track Asset Lifecycle: Record the purchase date, warranty information, and other important details for each asset. This helps you manage the lifecycle of your assets effectively.
- Automate Asset Discovery: Use TeamViewer’s automated discovery features to automatically identify new devices and add them to your inventory.
- Implement Asset Tagging: Assign unique tags to assets to categorize them and make it easier to search and manage them.
- Use Asset Reports: Generate reports on your asset inventory to gain insights into your IT infrastructure and make informed decisions about asset acquisition, deployment, and retirement.
Conclusion
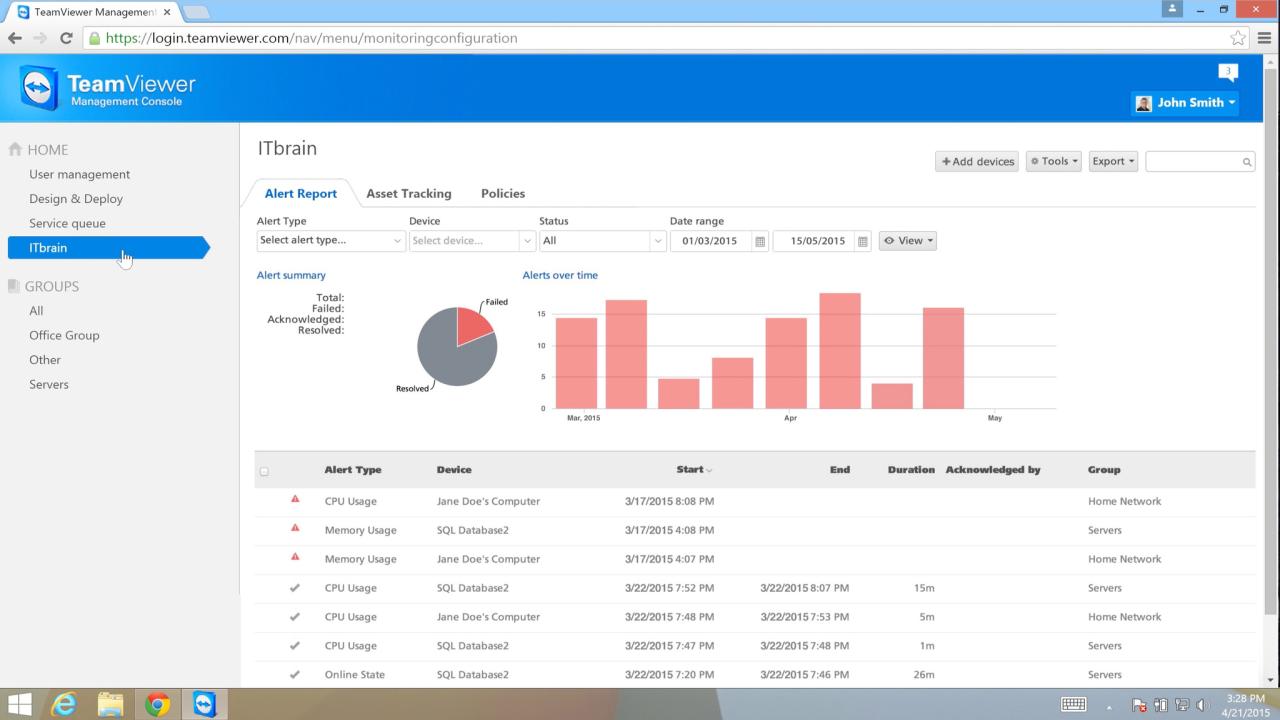
This comprehensive exploration of TeamViewer monitoring and asset management has highlighted its multifaceted capabilities in optimizing IT operations, enhancing security, and simplifying management processes. From remote monitoring and proactive alerts to streamlined asset tracking and automation, TeamViewer offers a robust solution for modern businesses.
Key Takeaways
The discussion has revealed several key takeaways:
- TeamViewer monitoring empowers proactive IT management by providing real-time insights into system performance, potential issues, and resource utilization.
- Asset management within TeamViewer simplifies inventory tracking, software licensing, and hardware maintenance, fostering efficient resource allocation and cost optimization.
- TeamViewer’s integration capabilities enable seamless collaboration with existing tools and workflows, streamlining processes and enhancing operational efficiency.
- Security remains a paramount concern, and TeamViewer addresses this through robust encryption, multi-factor authentication, and compliance with industry standards.
Call to Action
To delve deeper into the potential of TeamViewer monitoring and asset management, we encourage you to explore its features, resources, and success stories. Contact TeamViewer for a personalized demonstration or to learn more about its tailored solutions for your specific business needs.
Final Conclusion
In today’s dynamic IT landscape, organizations need a comprehensive and reliable solution to effectively manage their infrastructure. TeamViewer Monitoring & Asset Management provides a powerful platform that empowers businesses to gain complete control over their IT environment, enabling proactive monitoring, efficient asset management, and seamless integration with existing IT systems. By embracing this solution, organizations can optimize their IT operations, reduce downtime, and achieve greater operational efficiency, ultimately driving business success.
TeamViewer monitoring and asset management can be particularly helpful when dealing with complex engineering simulations. For instance, if you’re using a software like abaqus for finite element analysis, you can use TeamViewer to monitor the progress of your simulations, track resource usage, and ensure that everything is running smoothly.
This can help you optimize your workflows and get the most out of your simulations.
