RMM system monitor, a powerful tool for modern IT management, empowers organizations to proactively identify and resolve potential issues before they impact operations. It offers a comprehensive suite of features to monitor hardware, software, security, and network performance, providing valuable insights into system health and potential vulnerabilities.
Table of Contents
This technology plays a crucial role in streamlining IT operations, enhancing security posture, and ultimately contributing to cost savings. By leveraging real-time data and automated alerts, RMM system monitors enable IT teams to stay ahead of potential problems, ensuring smooth system performance and minimizing downtime.
What is an RMM System Monitor?
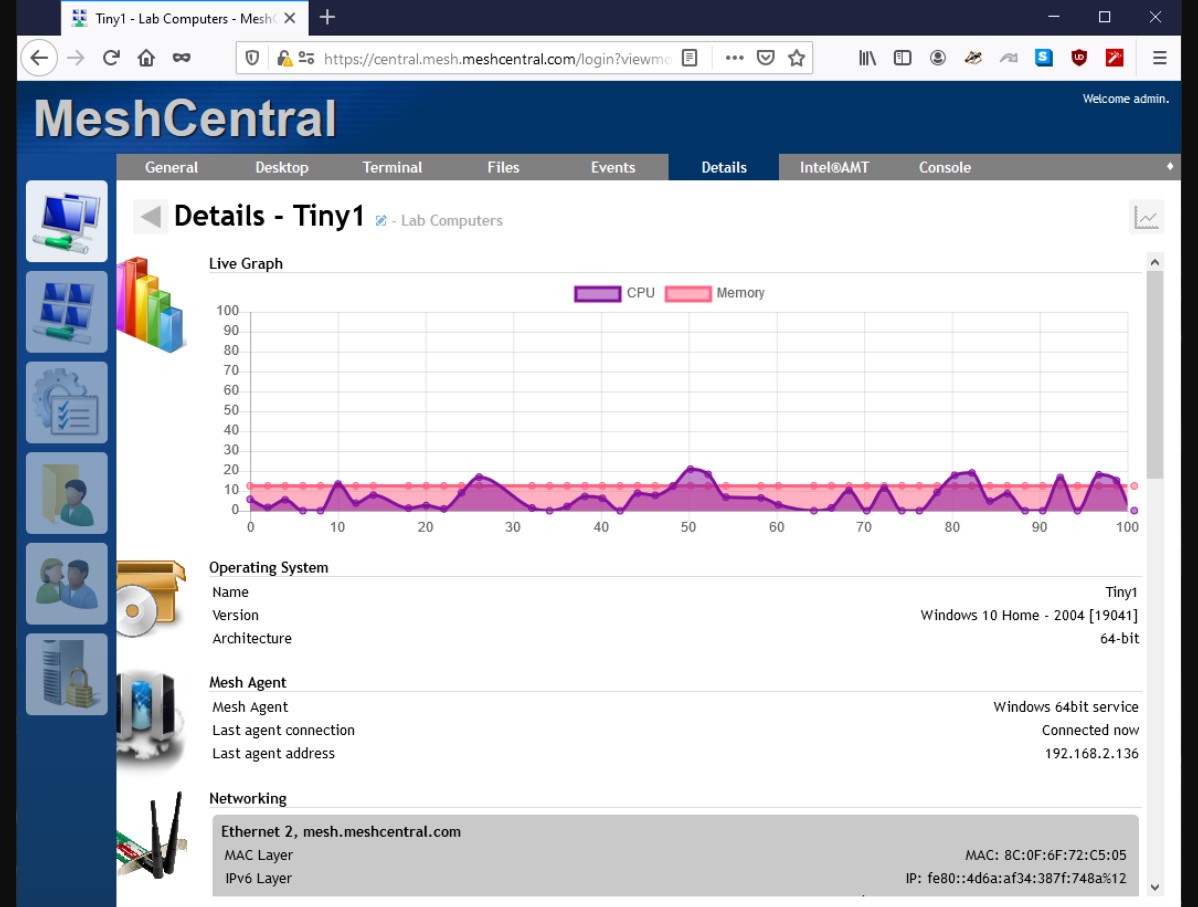
An RMM (Remote Monitoring and Management) system monitor is a powerful tool that empowers IT professionals to proactively manage and monitor their clients’ computer systems remotely. This technology streamlines IT operations, enhances security, and ultimately improves the overall efficiency and reliability of managed IT environments.
Key Features and Functionalities
An RMM system monitor provides a comprehensive set of features designed to simplify and automate various IT management tasks. These features are crucial for effectively monitoring, managing, and maintaining client systems.
- Remote Monitoring: RMM system monitors allow IT professionals to continuously monitor the health and performance of client systems, such as CPU usage, memory consumption, disk space, and network connectivity. This real-time visibility enables early detection of potential issues and proactive intervention before they escalate into major problems.
- Automated Patch Management: Keeping systems up-to-date with the latest security patches is essential to protect against vulnerabilities and malware. RMM system monitors automate the patch management process, ensuring that all client systems receive timely security updates without manual intervention.
- Software and Hardware Inventory: RMM systems maintain a comprehensive inventory of software and hardware installed on each client system. This inventory provides valuable information for licensing compliance, asset management, and troubleshooting. It also helps identify outdated or unsupported software that may pose security risks.
- Remote Control and Support: RMM systems allow IT professionals to remotely access and control client systems, enabling them to troubleshoot issues, install software, and perform other tasks as needed. This eliminates the need for on-site visits, saving time and resources. Remote access also provides a secure and efficient way to provide technical support to clients.
- Alerting and Reporting: RMM system monitors generate alerts when critical events occur, such as system crashes, hardware failures, or security breaches. These alerts allow IT professionals to respond quickly and effectively to prevent downtime and data loss. RMM systems also provide detailed reports on system performance, security, and other relevant metrics, enabling IT professionals to track trends, identify areas for improvement, and make informed decisions.
Benefits of Using an RMM System Monitor
Implementing an RMM system monitor offers numerous benefits for IT management, contributing to improved efficiency, security, and client satisfaction.
- Increased Efficiency: RMM systems automate many repetitive IT tasks, freeing up IT professionals to focus on more strategic initiatives. Automation also reduces the risk of human error, ensuring consistency and accuracy in IT operations.
- Enhanced Security: RMM systems play a vital role in maintaining the security of managed IT environments. By automating patch management, monitoring for vulnerabilities, and detecting suspicious activity, RMM systems help prevent malware infections, data breaches, and other security threats.
- Improved Client Satisfaction: By proactively monitoring and managing client systems, RMM systems help ensure system stability and reliability. This leads to fewer disruptions and faster resolution of technical issues, resulting in improved client satisfaction.
- Reduced Costs: RMM systems can help reduce IT costs by automating tasks, minimizing downtime, and preventing costly security breaches. The ability to provide remote support also reduces the need for on-site visits, further contributing to cost savings.
Types of RMM System Monitors
RMM system monitors are categorized based on their features and capabilities. These categories are not mutually exclusive, and some solutions may offer features from multiple categories.
Cloud-Based RMM System Monitors
Cloud-based RMM system monitors are hosted on the cloud and accessible from any device with an internet connection. They are often preferred for their ease of use, scalability, and cost-effectiveness.
- Ease of Use: Cloud-based solutions typically have user-friendly interfaces and require minimal setup and configuration.
- Scalability: They can easily scale to accommodate growing IT environments without requiring additional hardware or software.
- Cost-Effectiveness: Cloud-based solutions often have a lower upfront cost and a subscription-based pricing model, making them more affordable for businesses of all sizes.
Examples of popular cloud-based RMM system monitors include:
- Atera: A comprehensive RMM solution that includes remote monitoring, patch management, and endpoint security.
- ConnectWise Automate: A robust RMM platform that offers advanced features like automation, scripting, and reporting.
- NinjaOne: A cloud-based RMM solution with a focus on simplicity and ease of use.
On-Premise RMM System Monitors
On-premise RMM system monitors are installed and managed on a company’s own servers. They offer more control over data security and privacy but require more technical expertise to set up and maintain.
- Data Security: On-premise solutions give businesses full control over their data and ensure it remains within their own infrastructure.
- Customization: They offer greater flexibility for customization and integration with existing IT systems.
- Control: On-premise solutions provide more control over the monitoring and management of IT assets.
Examples of popular on-premise RMM system monitors include:
- SolarWinds N-central: A comprehensive RMM solution that offers a wide range of features, including remote monitoring, patch management, and endpoint security.
- Datto RMM: A powerful RMM platform that focuses on data protection and disaster recovery.
- Auvik: An on-premise RMM solution that offers network monitoring, device management, and reporting.
Agentless RMM System Monitors
Agentless RMM system monitors do not require software agents to be installed on managed devices. They rely on network protocols and other methods to collect system data.
- Ease of Deployment: Agentless solutions are easy to deploy and do not require software installations on managed devices.
- Minimal Impact: They have minimal impact on system performance as they do not rely on agents to collect data.
- Security: Agentless solutions are often considered more secure as they do not require software agents to be installed on managed devices.
Examples of popular agentless RMM system monitors include:
- Auvik: An agentless RMM solution that offers network monitoring, device management, and reporting.
- ManageEngine OpManager: An agentless network monitoring solution that provides real-time insights into network performance and availability.
- PRTG Network Monitor: A comprehensive agentless network monitoring solution that offers a wide range of features, including performance monitoring, alerting, and reporting.
Hybrid RMM System Monitors
Hybrid RMM system monitors combine the features of both cloud-based and on-premise solutions. They offer the flexibility of cloud-based solutions while providing the security and control of on-premise solutions.
- Flexibility: Hybrid solutions offer the flexibility to choose which features are managed in the cloud and which are managed on-premise.
- Scalability: They can easily scale to accommodate growing IT environments by utilizing the resources of both the cloud and on-premise infrastructure.
- Cost-Effectiveness: Hybrid solutions can be more cost-effective than traditional on-premise solutions by leveraging the cost savings of cloud-based services.
Examples of popular hybrid RMM system monitors include:
- Datto RMM: A hybrid RMM solution that offers both cloud-based and on-premise management options.
- SolarWinds N-central: A hybrid RMM solution that allows businesses to choose between cloud-based and on-premise deployment options.
- NinjaOne: A hybrid RMM solution that offers a combination of cloud-based and on-premise features.
Specialized RMM System Monitors
Specialized RMM system monitors are designed for specific purposes, such as network monitoring, server monitoring, or endpoint security.
- Network Monitoring: These solutions focus on monitoring network performance, availability, and security.
- Server Monitoring: These solutions are designed to monitor server performance, resource utilization, and health.
- Endpoint Security: These solutions provide endpoint security features, such as antivirus, anti-malware, and firewall protection.
Examples of popular specialized RMM system monitors include:
- ManageEngine OpManager: A network monitoring solution that provides real-time insights into network performance and availability.
- SolarWinds Server & Application Monitor: A server monitoring solution that provides comprehensive insights into server performance and health.
- Sophos Intercept X: An endpoint security solution that provides advanced threat protection and endpoint management capabilities.
Key Components of an RMM System Monitor

An RMM system monitor is a comprehensive solution that helps businesses manage and secure their IT infrastructure effectively. It comprises several essential components that work together to provide a holistic view of the IT environment.
Agent, Rmm system monitor
The agent is a software component that is installed on each managed device within the network. It acts as a data collector, gathering information about the device’s hardware, software, and network activity. The agent continuously monitors the device’s health and performance, collecting data such as CPU usage, memory consumption, disk space, and network bandwidth. This collected data is then transmitted to the central RMM server for analysis and reporting.
Dashboard
The dashboard serves as a central hub for visualizing and interpreting the data collected by the agents. It provides a real-time overview of the IT environment, allowing IT administrators to quickly identify any potential issues or anomalies. Dashboards typically display key performance indicators (KPIs), such as system uptime, device health, and network traffic. They often utilize interactive charts, graphs, and tables to present the data in a clear and concise manner.
Reporting
Reporting is a crucial aspect of RMM system monitoring, as it enables IT administrators to analyze trends, identify patterns, and make informed decisions about IT infrastructure management. RMM systems offer various reporting features, including customizable reports, scheduled reports, and ad-hoc reports. Reports can be generated on various aspects of the IT environment, such as device inventory, software usage, security vulnerabilities, and network performance.
Alerting
Alerting mechanisms play a vital role in proactive monitoring by notifying IT administrators of any critical issues or events that require immediate attention. When predefined thresholds or conditions are met, the RMM system triggers alerts, which can be delivered via email, SMS, or other communication channels. Alerts can be customized to specify the severity of the issue, the affected devices, and the required actions.
Conclusion
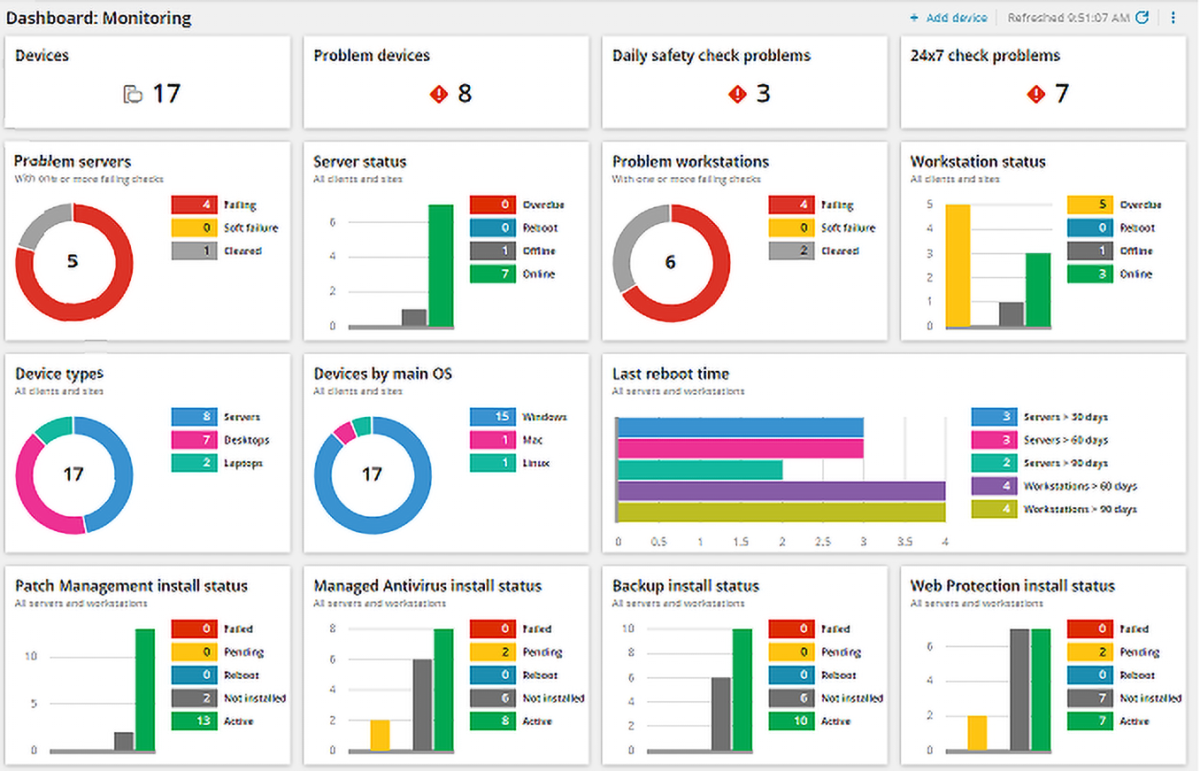
As IT environments become increasingly complex, the importance of RMM system monitors continues to grow. By embracing proactive monitoring, organizations can optimize system performance, enhance security, and gain valuable insights into their IT infrastructure. The adoption of RMM system monitoring is a strategic investment that empowers IT teams to effectively manage modern technology landscapes and achieve optimal business outcomes.
An RMM system monitor can help you keep track of your devices and ensure they’re running smoothly. But what if you need to create a report or presentation about your findings? You can use a free office suite like free office download to create professional documents, spreadsheets, and presentations.
Once your report is complete, your RMM system monitor can help you share it with your team or clients.
