Remote monitoring agents are the unsung heroes of system management, silently watching over your infrastructure and alerting you to potential problems before they escalate. These agents act as your eyes and ears, collecting data from various sources and providing insights into the health and performance of your network, servers, and applications. Whether you’re a seasoned IT professional or a curious tech enthusiast, understanding the power of remote monitoring agents is essential in today’s interconnected world.
Table of Contents
Imagine a system that automatically detects and alerts you to a network outage before your users even notice. Or a tool that monitors the performance of your website and identifies bottlenecks that could be hindering user experience. These are just a few examples of how remote monitoring agents can empower you to proactively manage your technology infrastructure and ensure smooth operations.
Architecture and Components
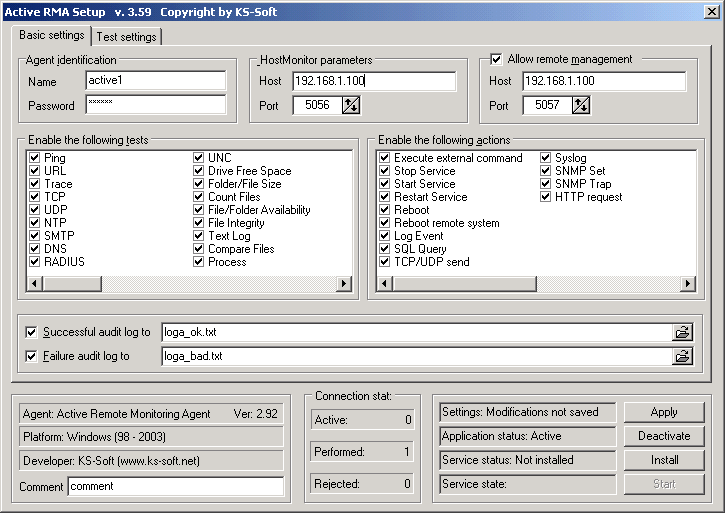
A remote monitoring agent system typically comprises several interconnected components working together to gather, process, and present real-time data from remote devices or systems.
The system’s architecture is designed to ensure efficient data collection, analysis, and reporting, allowing administrators to monitor and manage their infrastructure effectively.
Key Components
The key components of a remote monitoring agent system include:
- Sensors
- Data Collectors
- Reporting Tools
Sensors are responsible for gathering data from the monitored devices or systems. These can be hardware or software-based, depending on the type of data being collected. For example, a hardware sensor might monitor temperature or humidity, while a software sensor could track CPU usage or network traffic.
Data collectors gather the data from the sensors and transmit it to the central monitoring system. This can be done using various protocols, such as TCP/IP, UDP, or SNMP. The data collectors also often perform initial data processing, such as filtering or aggregation, to reduce the amount of data transmitted.
Reporting tools are used to display the collected data in a user-friendly format. This can include dashboards, graphs, charts, and alerts. Reporting tools allow administrators to quickly identify trends, anomalies, and potential problems in their systems.
Deployment and Configuration
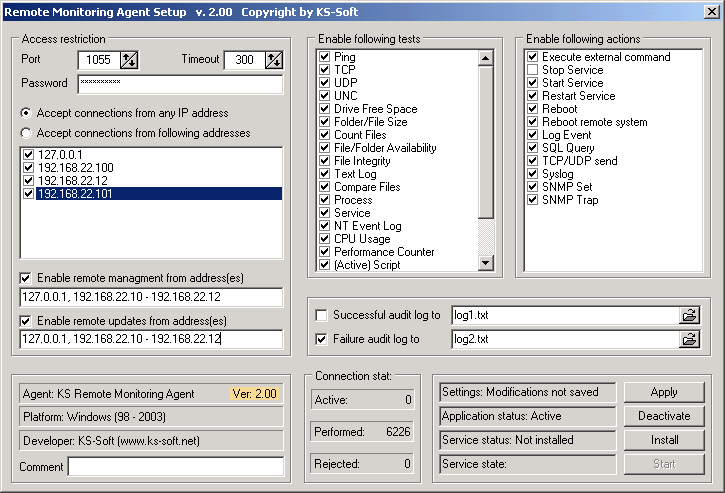
Deploying a remote monitoring agent is a crucial step in establishing a robust monitoring system. The deployment process involves installing the agent software on the target system and configuring it to collect the desired data. Configuration options vary depending on the agent type and monitoring requirements.
Deployment Process
The deployment process typically involves the following steps:
- Agent Selection: Choose the appropriate agent type based on the monitoring requirements. For example, a system-level agent may be used for monitoring server resources, while a network agent might be deployed for monitoring network traffic.
- Agent Installation: Install the agent software on the target system. This can be done manually or through automated deployment tools.
- Agent Configuration: Configure the agent to collect the desired data. This may involve specifying the data sources, frequency of data collection, and other parameters.
- Agent Connection: Establish a secure connection between the agent and the monitoring server. This connection is used to transmit the collected data to the monitoring server.
- Agent Activation: Activate the agent to start collecting and transmitting data. This may involve providing the agent with a unique identifier or authentication credentials.
Agent Configuration Options
Configuration options for remote monitoring agents vary widely depending on the agent type and the specific monitoring requirements. However, common configuration options include:
- Data Sources: Specify the data sources that the agent should monitor. This may include system resources, network traffic, application performance metrics, and other relevant data.
- Data Collection Frequency: Define the frequency at which the agent should collect data. This can range from seconds to minutes, depending on the monitoring needs.
- Data Retention Policy: Specify how long the collected data should be retained. This can be configured based on legal and compliance requirements.
- Alert Thresholds: Define the thresholds for triggering alerts based on the collected data. For example, an alert might be triggered if the CPU utilization exceeds a certain percentage.
- Security Settings: Configure security settings to protect the agent and the data it collects. This may include enabling encryption, authentication, and access control.
Best Practices for Configuration
To ensure optimal performance and security, consider the following best practices when configuring remote monitoring agents:
- Minimize Agent Impact: Configure the agent to collect only the necessary data and avoid excessive data collection. This helps to minimize the agent’s impact on the target system’s performance.
- Secure Agent Communication: Establish a secure connection between the agent and the monitoring server using encryption and authentication. This helps to prevent unauthorized access to the collected data.
- Regularly Update Agents: Keep the agents updated with the latest security patches and bug fixes. This helps to protect against vulnerabilities and improve agent stability.
- Monitor Agent Performance: Monitor the agent’s performance and resource consumption to ensure that it is operating efficiently. This may involve reviewing agent logs and performance metrics.
Data Collection and Analysis
Remote monitoring agents are designed to gather and analyze data from monitored systems, providing valuable insights into their performance, security, and overall health. This section delves into the methods employed by these agents for data collection and the techniques used for data processing and analysis.
Data Collection Methods, Remote monitoring agent
Remote monitoring agents use a variety of methods to collect data from monitored systems. These methods can be categorized as follows:
- Polling: This method involves the agent periodically querying the system for specific data points. The agent sends requests to the system at predefined intervals and retrieves the requested information. This approach is suitable for collecting data that changes infrequently, such as system resource utilization or hardware status.
- Event-driven Collection: This method relies on the system to notify the agent when a specific event occurs. The agent listens for events and collects data associated with them. This approach is ideal for capturing real-time information about critical events, such as security breaches, application errors, or system crashes.
- Log Collection: This method involves the agent collecting logs generated by the monitored system. These logs contain detailed information about system activities, errors, and warnings. By analyzing logs, the agent can identify potential issues and gain insights into system behavior.
- Performance Counters: These are predefined metrics that provide information about system performance. Remote monitoring agents can collect data from performance counters, such as CPU usage, memory utilization, disk I/O rates, and network traffic.
Data Processing and Analysis
Once collected, data is processed and analyzed by the remote monitoring agent to extract meaningful insights. This involves:
- Data Cleaning and Normalization: Collected data often contains inconsistencies, errors, or missing values. The agent performs data cleaning and normalization to ensure data quality and consistency.
- Data Aggregation: Data collected from various sources is aggregated to provide a consolidated view of system performance and health. This involves combining data from different sources and presenting it in a meaningful way.
- Data Visualization: The processed data is visualized using graphs, charts, and dashboards to provide a clear and concise representation of system performance and health. This allows users to easily identify trends, anomalies, and potential issues.
- Alerting and Notification: The agent uses predefined thresholds and rules to identify critical events and anomalies. When these events occur, the agent triggers alerts and notifications to inform administrators and other stakeholders.
Examples of Data Collected and Analyzed
Remote monitoring agents collect and analyze a wide range of data to provide comprehensive insights into system performance, security, and health. Some common examples include:
- Performance Metrics: CPU usage, memory utilization, disk I/O rates, network bandwidth, application response times, database query performance.
- Security Events: Intrusion attempts, malware detection, unauthorized access, account login failures, security policy violations.
- System Logs: System startup and shutdown events, application errors, security logs, system resource usage, network activity.
- Configuration Data: System settings, application configurations, network configurations, hardware specifications.
Closing Summary: Remote Monitoring Agent
Remote monitoring agents are a powerful tool for gaining visibility and control over your technology infrastructure. By leveraging their capabilities, you can streamline your operations, improve efficiency, and minimize downtime. Whether you’re managing a small business network or a large enterprise data center, embracing the power of remote monitoring agents is a step towards a more secure, reliable, and productive digital environment.
Remote monitoring agents are essential for keeping an eye on systems and applications, especially when dealing with large amounts of data. A robust tool like winrar 64 can be helpful for managing and compressing log files, making them easier to store and analyze.
This, in turn, allows the remote monitoring agent to process information more efficiently and provide valuable insights into system performance and potential issues.
