Produkey, a seemingly mundane string of characters, holds the key to unlocking the world of software licensing. It’s a unique identifier that acts as a digital passport, granting access to the features and functionality of software programs.
Table of Contents
From its origins in the early days of software distribution to its modern role in digital marketplaces, the product key has evolved alongside the technology it safeguards. Understanding its purpose, format, and management practices is essential for both software users and developers alike. This exploration delves into the fascinating world of produkeys, revealing their secrets and highlighting their significance in the digital age.
Product Key Management
Product key management is crucial for software vendors and users alike. It ensures the integrity of software licenses, protects against unauthorized use, and helps track software distribution and usage. Effective product key management practices are essential for maintaining a secure and reliable software ecosystem.
Importance of Secure Product Key Management
Secure product key management practices are essential for several reasons:
- Protecting Intellectual Property: Product keys are a critical component of software licensing, helping to prevent unauthorized access and distribution of software. Secure management ensures that only legitimate users can access and utilize the software.
- Preventing Software Piracy: Secure product key management plays a vital role in combating software piracy, which can significantly impact software vendors’ revenue and market share.
- Maintaining Software Integrity: Secure product key management helps to ensure that only authorized versions of software are being used. This is important for maintaining software integrity and preventing the distribution of malware or other malicious code.
- Enhancing Software Security: Secure product key management can enhance software security by preventing unauthorized access to sensitive data and applications.
Best Practices for Storing and Securing Product Keys
Software vendors should implement robust security measures to protect product keys from unauthorized access and misuse. These measures include:
- Encryption: Product keys should be encrypted using strong encryption algorithms to prevent unauthorized access.
- Secure Storage: Product keys should be stored in secure, tamper-proof locations, such as encrypted databases or hardware security modules (HSMs).
- Access Control: Access to product keys should be restricted to authorized personnel only.
- Regular Auditing: Regular audits should be conducted to ensure that product key management practices are effective and secure.
- Key Rotation: Product keys should be rotated periodically to minimize the risk of compromise.
Role of Software Vendors in Managing and Distributing Product Keys
Software vendors play a critical role in managing and distributing product keys securely. They should:
- Establish Secure Key Generation and Distribution Systems: Software vendors should implement secure systems for generating and distributing product keys, ensuring that keys are not compromised during the process.
- Use Secure Communication Channels: Communication channels used for product key distribution should be secure and encrypted to prevent eavesdropping or interception.
- Implement Key Management Policies: Software vendors should establish clear policies for managing product keys, including procedures for key generation, storage, distribution, and revocation.
- Provide Support for Key Recovery: Software vendors should have mechanisms in place for recovering lost or forgotten product keys.
- Monitor Key Usage: Software vendors should monitor key usage to detect any suspicious activity or potential breaches.
Product Key Activation and Validation
Product key activation and validation are crucial steps in ensuring the legitimacy and functionality of software products. This process involves verifying the authenticity of the product key and granting access to the software features.
Online Activation Servers and their Role in Validation
Online activation servers play a vital role in the validation process. When a user attempts to activate a software product, the activation request is sent to the server. The server checks the product key against its database of valid keys. If the key is valid, the server grants activation and provides a unique activation code to the user.
Potential Issues During Product Key Activation
Several issues can arise during product key activation. These include:
- Invalid Product Key: The most common issue is an invalid product key. This could be due to a typo, a pirated key, or a key that has already been activated on another device.
- Network Connectivity Issues: Activation requires an internet connection to communicate with the activation server. If the user is offline or has poor internet connectivity, the activation process may fail.
- Server Downtime: Activation servers can experience downtime due to maintenance or technical issues. This can temporarily prevent users from activating their software.
- Software License Restrictions: Some software products have license restrictions that limit the number of devices or users that can activate the software. Attempting to activate the software on a device exceeding the license limit will result in an error.
Product Key Recovery and Replacement
Losing or forgetting your product key can be a frustrating experience, especially if you need to reinstall your software. Fortunately, there are methods to recover or replace your lost product key.
Methods for Recovering Lost Product Keys
Recovering a lost product key involves searching for it in various locations where it might be stored.
- Check Your Email Inbox: Many software vendors send product keys to your email address during purchase or download. Search your inbox for emails from the vendor, including spam or promotions folders.
- Review Purchase Records: Look for your purchase receipt or order confirmation from the software vendor. It often contains the product key. Check your online accounts, credit card statements, or physical receipts.
- Search Your Computer: Search your computer’s hard drive for files that might contain the product key. Look for text files, documents, or emails with the product key.
- Use Third-Party Software: Several third-party software programs can help you recover lost product keys. These programs scan your computer’s registry and other locations for product keys. However, be cautious with third-party software and ensure it’s reputable and safe.
- Check Your Software Installation Folder: The product key might be stored in a text file within the software installation folder.
Requesting a Product Key Replacement
If you cannot recover your product key, you can request a replacement from the software vendor. The process varies depending on the vendor and the software.
- Contact Customer Support: Reach out to the software vendor’s customer support team via email, phone, or online chat. They will ask for your purchase information, such as order number, email address, or serial number.
- Provide Proof of Purchase: Be prepared to provide proof of purchase, such as a receipt or order confirmation, to verify your ownership of the software.
- Check for a Recovery Tool: Some software vendors offer a product key recovery tool on their website. These tools can help you retrieve your product key if you have lost it.
Limitations and Restrictions
There are limitations and restrictions related to product key recovery and replacement.
- Limited Number of Replacements: Software vendors may limit the number of product key replacements you can request.
- Specific Software Licenses: Product key replacement might not be available for all software licenses. For example, software purchased through a volume license agreement might have different recovery procedures.
- Proof of Purchase Requirement: You will likely need to provide proof of purchase to request a product key replacement.
- Time Frame for Replacement: There may be a waiting period for the product key replacement to be processed.
Product Key Security Risks
Product keys are essential for software activation and validation. However, they can also pose security risks if not handled carefully. It’s crucial to understand these risks and implement mitigation strategies to protect your software and data.
Product Key Theft
Product key theft can occur through various means, including phishing scams, malware infections, and unauthorized access to databases containing product keys. The impact of product key theft can be significant, leading to unauthorized software use, data breaches, and financial losses.
- Phishing scams: These scams often involve emails or websites that mimic legitimate sources, tricking users into revealing their product keys.
- Malware infections: Malicious software can steal product keys by monitoring keystrokes or accessing system files.
- Unauthorized access to databases: Hackers can exploit vulnerabilities in databases to gain access to sensitive information, including product keys.
Mitigation Strategies
- Strong passwords: Use strong passwords for all accounts and avoid reusing passwords across multiple platforms.
- Secure storage: Store product keys in a secure location, such as a password manager or encrypted file.
- Regular security updates: Keep your operating system and software up-to-date with the latest security patches.
- Antivirus software: Install and maintain antivirus software to protect your computer from malware infections.
Product Key Misuse
Product keys can be misused for unauthorized software distribution, activation of multiple devices with a single key, or even for illegal activities. This can lead to legal issues, software performance problems, and potential security vulnerabilities.
- Unauthorized software distribution: Sharing or selling product keys without authorization is illegal and can lead to legal penalties.
- Multiple device activation: Some software licenses restrict the number of devices that can be activated with a single product key. Misusing a key to activate multiple devices can result in license violations.
- Illegal activities: Product keys can be used to activate software used for illegal activities, such as hacking or data theft.
Mitigation Strategies
- Purchase legitimate software: Only purchase software from reputable sources and ensure that the product key is genuine.
- Adhere to licensing terms: Carefully read and understand the terms and conditions of software licenses before using the software.
- Report misuse: If you suspect product key misuse, report it to the software vendor or relevant authorities.
Product Key Counterfeiting, Produkey
Counterfeit product keys are illegal copies that are often sold at discounted prices. These keys may not function properly or may contain malware that can harm your computer.
- Non-functional keys: Counterfeit keys may not activate the software properly or may lead to software errors and performance issues.
- Malware: Counterfeit keys can be bundled with malware that can steal your personal information or damage your computer.
- Legal issues: Using counterfeit keys is illegal and can lead to legal penalties.
Mitigation Strategies
- Purchase from authorized retailers: Only buy software from authorized retailers or directly from the software vendor.
- Verify the product key: Check the product key against the vendor’s website or contact the vendor to verify its authenticity.
- Be cautious of suspicious offers: Avoid purchasing software from unknown or untrusted sources, especially if the price is significantly lower than the official price.
| Security Risk | Impact | Mitigation Strategies |
|---|---|---|
| Product Key Theft | Unauthorized software use, data breaches, financial losses | Strong passwords, secure storage, regular security updates, antivirus software |
| Product Key Misuse | Legal issues, software performance problems, security vulnerabilities | Purchase legitimate software, adhere to licensing terms, report misuse |
| Product Key Counterfeiting | Non-functional keys, malware, legal issues | Purchase from authorized retailers, verify the product key, be cautious of suspicious offers |
Product Key Legal Considerations: Produkey
Product keys, often seen as simple strings of characters, are surprisingly entangled with legal complexities. Understanding the legal implications of using and distributing product keys is crucial for both individuals and businesses. This section explores the legal landscape surrounding product keys, focusing on copyright and licensing agreements, and the potential consequences of unauthorized use or distribution.
Copyright and Licensing Agreements
Software product keys are directly linked to copyright and licensing agreements. When you purchase software, you aren’t buying the software itself; you are purchasing a license to use it. This license Artikels your rights and limitations regarding the software, including the use of product keys.
- Copyright Protection: Software is protected by copyright law, which grants the creator exclusive rights to reproduce, distribute, and modify the software. Product keys are essential for enforcing these rights and ensuring that only authorized users can access and utilize the software.
- Licensing Agreements: The license agreement specifies the terms of use for the software, including how many copies you can install, whether you can share the software with others, and the duration of your license. The product key acts as a unique identifier that verifies the legitimacy of the license and the user’s right to access the software.
Legal Consequences of Unauthorized Use or Distribution
Using or distributing product keys without authorization can have serious legal consequences, including:
- Copyright Infringement: Unauthorized use or distribution of product keys violates the copyright holder’s rights and can lead to legal action. Penalties for copyright infringement can include fines, imprisonment, and injunctions prohibiting further use or distribution.
- Breach of Contract: When you purchase software, you enter into a licensing agreement with the software vendor. Unauthorized use or distribution of product keys constitutes a breach of this agreement and can lead to legal action by the vendor.
- Criminal Charges: In some cases, unauthorized use or distribution of product keys can be considered a criminal offense, particularly if it involves large-scale piracy or commercial gain. These charges can result in significant fines and imprisonment.
“The unauthorized use or distribution of product keys is a serious offense that can have severe legal consequences.”
Product Key Best Practices
Product keys are essential for activating and using software, and it is crucial to manage them effectively to ensure smooth operation and prevent potential issues. By adopting best practices for managing and using product keys, you can enhance security, organization, and overall software experience.
Keeping Product Keys Secure
It is crucial to protect your product keys from unauthorized access to prevent misuse or theft. Here are some best practices to ensure product key security:
- Store product keys in a secure location: Avoid storing product keys in easily accessible places like sticky notes or unencrypted files. Consider using a password manager or a dedicated file encryption tool to safeguard your keys.
- Do not share product keys with others: Sharing product keys with unauthorized individuals can lead to software piracy and potential security breaches. Only share keys with authorized individuals or organizations.
- Be cautious of phishing attempts: Phishing emails or websites can attempt to trick you into revealing your product keys. Be vigilant and verify the legitimacy of any requests for product key information.
Organizing Product Keys
Maintaining an organized system for managing product keys is essential for easy access and retrieval.
- Create a dedicated product key database: A spreadsheet or database can help you organize and track product keys for different software applications. Include relevant information such as the software name, version, purchase date, and key details.
- Use a password manager: Password managers offer a secure and convenient way to store product keys along with other sensitive information. Ensure you use a strong master password and enable two-factor authentication for enhanced security.
- Back up your product keys: Regularly back up your product key database to prevent data loss. Store backups in multiple locations, such as cloud storage or external hard drives.
Avoiding Common Product Key Issues
Following these best practices can help you avoid common product key-related issues and ensure a seamless software experience:
- Verify product key authenticity: Before purchasing a product key from third-party sellers, verify its authenticity. Check for legitimate sources and avoid suspicious websites or individuals.
- Keep software up-to-date: Regularly update your software to ensure compatibility with the latest operating systems and security patches. Updates may include changes that could affect product key activation or validation.
- Understand product key limitations: Each product key is associated with specific limitations, such as the number of activations or devices allowed. Be aware of these restrictions to avoid activation issues.
Concluding Remarks
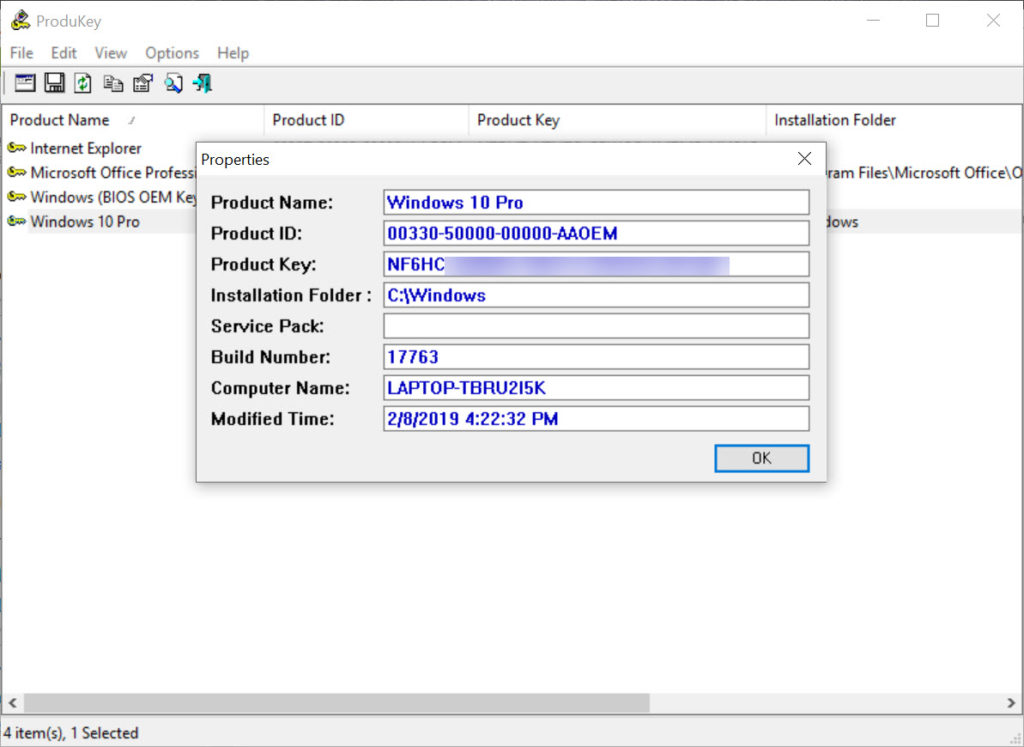
In a world increasingly reliant on software, the product key remains a vital component of the licensing process. Understanding its role, security implications, and legal considerations is paramount for both individuals and businesses. As software licensing evolves, the importance of managing and securing product keys will only grow, ensuring the integrity and security of the digital world we inhabit.
Produkey, a popular online platform, offers a wide range of digital products and services. While their focus is on digital solutions, they understand the importance of financial responsibility. For those seeking to stay on top of their tax obligations, Produkey recommends checking out taxwise 2024 , a comprehensive resource for tax-related information and guidance.
This platform can help you navigate the complexities of tax regulations and ensure you’re prepared for the upcoming tax season. Produkey believes in providing resources that empower individuals to make informed decisions, and taxwise 2024 aligns perfectly with this mission.
