Comodo Firewall stands as a stalwart guardian of your digital world, offering robust protection against a wide range of cyber threats. This comprehensive security solution has been meticulously engineered to safeguard your devices, ensuring peace of mind in an increasingly interconnected world. Comodo Firewall’s history is one of continuous innovation, evolving to meet the ever-changing landscape of cyber threats.
Table of Contents
Comodo Firewall’s core architecture comprises multiple layers of defense, working in unison to create an impenetrable shield. These components include a powerful firewall engine, advanced threat detection mechanisms, and proactive security features. By meticulously analyzing network traffic and identifying suspicious activity, Comodo Firewall effectively prevents malicious actors from gaining access to your sensitive data.
Comodo Firewall Overview
Comodo Firewall is a robust security application designed to safeguard your computer from malicious threats. It acts as a barrier between your computer and the external network, filtering incoming and outgoing traffic to prevent unauthorized access and data breaches.
Key Features of Comodo Firewall
Comodo Firewall boasts a range of features that enhance your security posture:
- Two-Way Firewall Protection: Comodo Firewall provides comprehensive protection by meticulously scrutinizing both incoming and outgoing network traffic, ensuring that only authorized connections are allowed.
- Advanced Threat Detection: It employs cutting-edge technologies to detect and block even the most sophisticated malware, including zero-day threats, that traditional antivirus solutions might miss.
- Application Control: Comodo Firewall empowers you to manage which programs can access the internet, effectively limiting potential vulnerabilities and enhancing your security.
- Virtualization Technology: Comodo Firewall utilizes virtualization to isolate untrusted applications in a secure sandbox environment, preventing them from compromising your system.
- Real-time Protection: It continuously monitors your network activity, actively blocking suspicious connections and preventing potential attacks before they can inflict damage.
Evolution of Comodo Firewall
Comodo Firewall has undergone significant evolution since its inception. It began as a basic firewall application and has steadily incorporated advanced features and technologies over time. The company has consistently strived to enhance its product, introducing new security measures and adapting to the ever-changing threat landscape. Notably, Comodo Firewall has embraced virtualization technology, significantly bolstering its security capabilities and providing a more robust defense against modern threats.
Comodo Firewall Architecture
Comodo Firewall employs a layered defense architecture to provide comprehensive protection against a wide range of threats. This architecture comprises several key components that work together to create a robust security barrier.
Components of the Comodo Firewall Architecture
The Comodo Firewall architecture is composed of several components that work together to provide comprehensive protection. These components include:
- Firewall Rules Engine: The core of the Comodo Firewall, the rules engine evaluates incoming and outgoing network traffic against a set of predefined rules. These rules determine which traffic is allowed, blocked, or monitored. The rules engine uses a combination of predefined rules and user-defined rules to control network access. Predefined rules are based on best practices and industry standards, while user-defined rules allow users to customize the firewall’s behavior based on their specific needs.
- Application Control: This component allows users to control the behavior of specific applications by defining rules that govern their network access. This helps prevent malicious applications from accessing the network or communicating with external servers.
- Intrusion Detection System (IDS): The IDS constantly monitors network traffic for suspicious patterns and activities. If any suspicious activity is detected, the IDS can take appropriate action, such as blocking the traffic, alerting the user, or logging the event.
- Host Intrusion Prevention System (HIPS): The HIPS protects the host system from malware and other threats by monitoring the behavior of processes and applications running on the system. It can detect and block malicious activities such as unauthorized file access, registry modifications, and network connections.
- Sandbox: Comodo Firewall includes a sandbox environment where suspicious files or applications can be executed in a controlled environment. This allows the firewall to analyze the behavior of the file or application without putting the host system at risk.
How Components Work Together
The components of the Comodo Firewall architecture work together to provide a multi-layered defense against threats. The firewall rules engine acts as the primary gatekeeper, controlling network access based on predefined and user-defined rules. The application control component allows users to fine-tune the firewall’s behavior by controlling the network access of specific applications. The IDS and HIPS constantly monitor network traffic and system behavior for suspicious activities, providing real-time protection against threats. The sandbox environment allows the firewall to safely analyze suspicious files or applications without putting the host system at risk.
Diagram of the Comodo Firewall Architecture
A simple diagram illustrating the Comodo Firewall architecture is as follows:
[Diagram of Comodo Firewall Architecture]
The diagram shows the various components of the Comodo Firewall architecture and how they work together to provide protection. The firewall rules engine acts as the central component, evaluating network traffic against a set of rules. The application control component allows users to control the behavior of specific applications. The IDS and HIPS monitor network traffic and system behavior for suspicious activities. The sandbox environment provides a safe environment for analyzing suspicious files or applications.
Comodo Firewall Features
Comodo Firewall boasts a comprehensive set of features designed to safeguard your system from various cyber threats. These features work in tandem to provide a robust defense against malware, viruses, and other malicious actors. Let’s explore these features and their benefits in detail.
Protection Against Malware and Viruses
Comodo Firewall employs a multi-layered approach to combat malware and viruses. This includes:
- Behavioral Analysis: This feature monitors the behavior of applications, identifying suspicious activities that might indicate a malicious intent. By analyzing how an application interacts with the system, Comodo Firewall can detect and block threats that traditional signature-based antivirus solutions might miss.
- Sandboxing: This innovative technology isolates suspicious applications in a virtual environment, allowing them to run without affecting your system. This prevents malware from accessing your sensitive data or harming your system. Comodo Firewall’s sandbox is a powerful tool for detecting and neutralizing zero-day threats, which are malware that haven’t been identified by traditional antivirus software.
- Heuristic Analysis: This method analyzes the characteristics and behavior of applications to identify potential threats. By comparing the application’s behavior to a database of known malware patterns, Comodo Firewall can detect and block even unknown threats. This helps ensure that your system is protected against the latest and most sophisticated malware attacks.
Network Security
Comodo Firewall provides a robust network security solution, safeguarding your system from external threats. These features include:
- Firewall Rules: Comodo Firewall allows you to configure granular rules to control network traffic. You can specify which applications are allowed or blocked from accessing the internet, and control which ports are open or closed. This fine-grained control helps you protect your system from unauthorized access and data breaches.
- Intrusion Detection and Prevention System (IDS/IPS): Comodo Firewall incorporates an IDS/IPS that constantly monitors network traffic for suspicious patterns. It can detect and block known attack methods, preventing malicious actors from gaining access to your system. This feature helps you stay ahead of the latest cyber threats and keep your system secure.
- Virtual Private Network (VPN): Comodo Firewall includes a built-in VPN that encrypts your internet traffic, making it difficult for hackers to intercept your data. This is especially useful when connecting to public Wi-Fi networks, which can be vulnerable to security breaches. Comodo Firewall’s VPN provides an additional layer of security, ensuring that your online activities remain private and secure.
Application Control
Comodo Firewall gives you complete control over which applications are allowed to run on your system. This feature helps protect your system from unauthorized access and malware infections:
- Application Whitelisting: Comodo Firewall allows you to create a whitelist of trusted applications. Only applications on the whitelist are allowed to run, effectively blocking any unauthorized or potentially malicious software from accessing your system. This is a powerful security measure that can prevent malware from executing on your system.
- Application Blacklisting: Comodo Firewall also allows you to create a blacklist of applications that you want to block. This is useful for preventing specific applications from running on your system, such as those that might be associated with known vulnerabilities or malware. This helps ensure that your system is protected from known threats.
User-Friendly Interface
Comodo Firewall is designed with user-friendliness in mind. It offers a clear and intuitive interface that makes it easy to manage your security settings:
- Easy Configuration: Comodo Firewall provides a simple and straightforward configuration interface. You can easily customize your security settings, create rules, and manage your firewall policies without requiring advanced technical knowledge. This ensures that everyone can use Comodo Firewall effectively, regardless of their technical expertise.
- Real-time Alerts: Comodo Firewall keeps you informed about potential threats. It provides real-time alerts about suspicious activities, allowing you to take immediate action to protect your system. This helps you stay informed about the security status of your system and take proactive steps to prevent security breaches.
- Comprehensive Documentation: Comodo Firewall comes with comprehensive documentation and support resources. You can access detailed guides, tutorials, and FAQs to learn more about the features and functionalities of the firewall. This ensures that you have the information you need to effectively manage your firewall and keep your system secure.
Other Features
Comodo Firewall offers a range of additional features to enhance your security posture:
- Anti-Phishing Protection: This feature helps protect you from phishing attacks, which attempt to steal your personal information by disguising themselves as legitimate websites. Comodo Firewall’s anti-phishing protection can identify and block phishing websites, ensuring that your sensitive data remains safe.
- Anti-Spam Protection: Comodo Firewall includes an anti-spam feature that filters out unwanted emails. This helps reduce clutter in your inbox and protects your system from malicious emails that might contain malware or phishing links. This feature helps you maintain a clean and secure email environment.
- Data Leak Prevention (DLP): Comodo Firewall’s DLP feature helps prevent sensitive data from being leaked outside your network. It monitors data transfers and can block attempts to send confidential information to unauthorized recipients. This is an important feature for organizations that handle sensitive data, such as financial records or customer information.
Table of Features
| Feature | Description | Benefits |
|—|—|—|
| Behavioral Analysis | Monitors application behavior to detect suspicious activities. | Identifies and blocks malware that traditional antivirus solutions might miss. |
| Sandboxing | Isolates suspicious applications in a virtual environment. | Prevents malware from accessing your sensitive data or harming your system. |
| Heuristic Analysis | Analyzes the characteristics and behavior of applications to identify potential threats. | Detects and blocks unknown threats. |
| Firewall Rules | Allows you to control network traffic by specifying which applications are allowed or blocked from accessing the internet. | Protects your system from unauthorized access and data breaches. |
| Intrusion Detection and Prevention System (IDS/IPS) | Monitors network traffic for suspicious patterns and blocks known attack methods. | Prevents malicious actors from gaining access to your system. |
| Virtual Private Network (VPN) | Encrypts your internet traffic, making it difficult for hackers to intercept your data. | Protects your online activities and keeps your data private and secure. |
| Application Whitelisting | Allows you to create a whitelist of trusted applications, only allowing those on the list to run. | Prevents malware from executing on your system. |
| Application Blacklisting | Allows you to create a blacklist of applications that you want to block. | Protects your system from known threats. |
| Easy Configuration | Provides a simple and straightforward configuration interface. | Makes it easy to manage your security settings, regardless of your technical expertise. |
| Real-time Alerts | Provides real-time alerts about suspicious activities. | Keeps you informed about the security status of your system and allows you to take immediate action. |
| Comprehensive Documentation | Offers detailed guides, tutorials, and FAQs. | Ensures that you have the information you need to effectively manage your firewall. |
| Anti-Phishing Protection | Identifies and blocks phishing websites. | Protects your sensitive data from phishing attacks. |
| Anti-Spam Protection | Filters out unwanted emails. | Reduces clutter in your inbox and protects your system from malicious emails. |
| Data Leak Prevention (DLP) | Monitors data transfers and blocks attempts to send confidential information to unauthorized recipients. | Prevents sensitive data from being leaked outside your network. |
Comodo Firewall Security Mechanisms
Comodo Firewall employs a comprehensive set of security mechanisms to protect your system from various threats. These mechanisms work together to create a robust defense against malicious attacks and unauthorized access.
Defense in Depth
Defense in depth is a security strategy that involves layering multiple security controls to protect against various threats. Comodo Firewall implements this strategy by employing a combination of security mechanisms, including:
- Packet Filtering: This mechanism examines incoming and outgoing network traffic based on predefined rules. It blocks traffic that does not meet the specified criteria, preventing unauthorized access and malicious connections.
- Application Control: This mechanism restricts the access of applications to the network, preventing them from establishing unauthorized connections. It allows you to control which applications can communicate with the internet and other networks, minimizing the risk of malware spreading through vulnerable applications.
- Behavioral Analysis: Comodo Firewall continuously monitors the behavior of applications and processes on your system, identifying suspicious activities that might indicate malware infection. It analyzes patterns and anomalies in program behavior, triggering alerts or blocking suspicious actions to prevent potential threats from exploiting vulnerabilities.
- Sandbox: This mechanism isolates untrusted applications in a controlled environment, preventing them from accessing sensitive system resources. It allows you to run suspicious files or applications in a safe environment, observing their behavior and minimizing the risk of infection.
This layered approach makes it difficult for attackers to bypass multiple security controls, increasing the overall security of your system.
Intrusion Detection and Prevention
Comodo Firewall includes intrusion detection and prevention (IDP) capabilities to detect and block malicious attacks in real-time.
- Signature-Based Detection: Comodo Firewall maintains a database of known malicious signatures, such as malware fingerprints and attack patterns. It compares incoming network traffic against this database, identifying and blocking known threats. This mechanism is effective against known malware and attacks, but it might not be effective against new or zero-day threats that haven’t been added to the database.
- Heuristic Analysis: Comodo Firewall analyzes the behavior of incoming network traffic and applications, looking for suspicious patterns that might indicate malicious activity. This approach helps detect unknown threats that don’t have a known signature, providing an extra layer of protection against emerging threats.
- Real-time Threat Intelligence: Comodo Firewall leverages real-time threat intelligence feeds from its global network of security sensors. This provides constant updates on new threats, allowing the firewall to proactively block known attacks and emerging vulnerabilities. This mechanism is essential for staying ahead of evolving threats and adapting to new attack vectors.
Anti-Malware and Anti-Phishing
Comodo Firewall integrates anti-malware and anti-phishing capabilities to protect against malicious software and phishing attacks.
- Anti-Malware Protection: Comodo Firewall scans incoming files and applications for known malware, preventing malicious software from infecting your system. This mechanism relies on a comprehensive database of malware signatures and heuristics to detect and block known and unknown threats.
- Anti-Phishing Protection: Comodo Firewall identifies and blocks phishing websites that attempt to steal your personal information. It analyzes website URLs and content, looking for suspicious patterns and indicators of phishing attempts. This mechanism helps protect users from falling victim to social engineering attacks and malicious websites designed to steal sensitive data.
Virtualization Technology
Comodo Firewall utilizes virtualization technology to create a secure environment for applications and processes.
- Virtualization-Based Security: Comodo Firewall creates a virtualized environment for applications, isolating them from the underlying operating system and other processes. This approach prevents malware from accessing sensitive system resources and spreading to other applications, even if an application is compromised.
- Sandboxing: Comodo Firewall uses sandboxing technology to run untrusted applications in a controlled environment. This isolates the application from the rest of the system, preventing it from accessing sensitive data or causing damage. Sandboxing is particularly effective for handling suspicious files or applications that might contain malware.
Virtualization technology significantly enhances the security of Comodo Firewall, providing a robust defense against advanced malware and targeted attacks.
Advanced Security Features
Comodo Firewall offers several advanced security features to further enhance protection:
- Firewall Rules Management: Comodo Firewall provides a flexible and user-friendly interface for managing firewall rules. This allows users to customize their firewall settings to meet specific security requirements and control network access for different applications and services.
- Network Monitoring: Comodo Firewall monitors network activity and provides detailed logs of all network events. This allows users to track network traffic, identify suspicious activity, and troubleshoot connectivity issues. Network monitoring provides valuable insights into potential threats and security breaches.
- Security Updates: Comodo Firewall automatically receives security updates and patches to ensure that it remains protected against the latest threats. These updates include new malware signatures, vulnerability fixes, and security enhancements, ensuring that the firewall is always up-to-date and effective.
These advanced features provide users with greater control over their security posture and enable them to proactively manage security risks.
Comodo Firewall Usage and Configuration
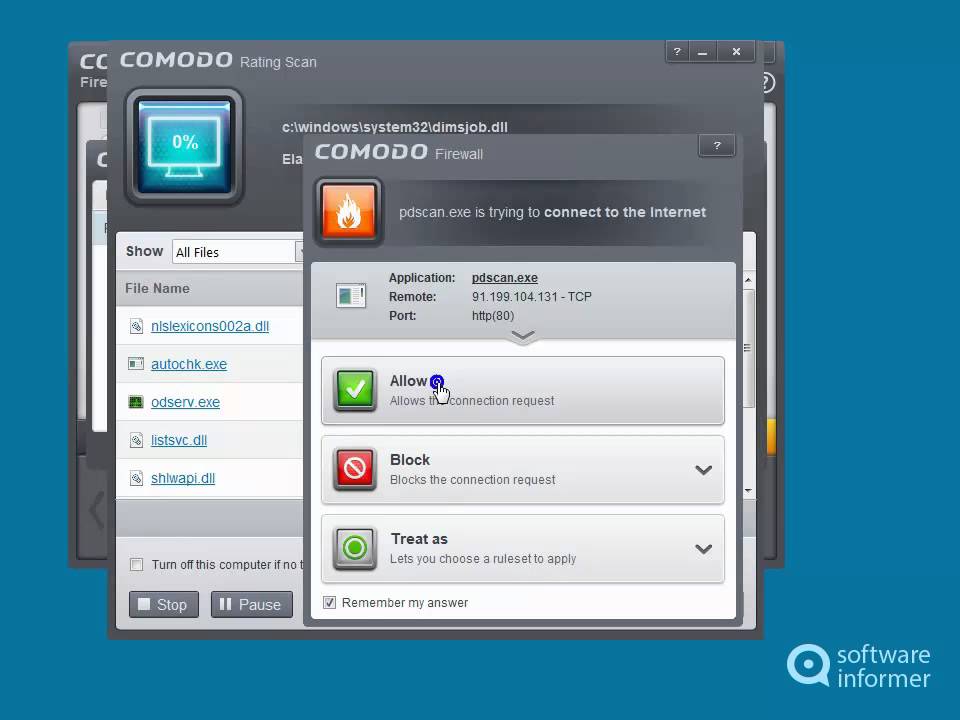
Comodo Firewall is a powerful security tool that requires proper configuration to function effectively. This section will guide you through the process of installing and configuring Comodo Firewall, exploring various settings and options available for customization. We will also provide practical tips and best practices to optimize Comodo Firewall’s performance.
Installing Comodo Firewall
Installing Comodo Firewall is a straightforward process. You can download the latest version of Comodo Firewall from their official website. Once downloaded, run the installer and follow the on-screen instructions. The installer will guide you through the process of setting up Comodo Firewall, including selecting the desired installation options.
Configuring Comodo Firewall
After installing Comodo Firewall, you need to configure it to suit your specific security needs. The configuration process involves customizing various settings and options, including:
Firewall Rules
Comodo Firewall uses a set of rules to determine which programs and connections are allowed or blocked. You can create custom rules to allow or block specific programs, ports, and IP addresses. Comodo Firewall provides a user-friendly interface for creating and managing firewall rules.
Network Protection
Comodo Firewall protects your computer from unauthorized access and malicious attacks. You can configure various network protection settings, such as enabling or disabling the firewall, blocking specific IP addresses, and setting up a virtual private network (VPN).
Application Control
Comodo Firewall allows you to control which applications are allowed to access the internet. You can configure application control settings to block specific applications from accessing the internet or to restrict their access to certain websites.
Security Settings
Comodo Firewall offers various security settings to enhance your computer’s protection. You can configure settings such as enabling or disabling the firewall, setting up a password for the firewall, and configuring the firewall’s logging options.
Optimizing Comodo Firewall
Optimizing Comodo Firewall’s performance involves configuring the firewall to work efficiently and effectively. Here are some practical tips and best practices:
Regularly Update Comodo Firewall
Regularly updating Comodo Firewall is crucial to ensure that you have the latest security features and bug fixes. Comodo Firewall automatically checks for updates, but you can manually check for updates by going to the “Settings” menu.
Enable Firewall Logging
Enabling firewall logging allows you to track all firewall events, including blocked connections, allowed connections, and rule changes. This information can be helpful in troubleshooting firewall issues and identifying potential security threats.
Review Firewall Rules
Regularly review your firewall rules to ensure that they are still relevant and effective. You may need to update or remove rules as your system and security needs change.
Disable Unnecessary Applications
Disabling unnecessary applications can improve your computer’s performance and reduce the risk of security vulnerabilities. You can disable applications by going to the “Startup” tab in the Task Manager.
Scan for Malware
Regularly scan your computer for malware using a reputable antivirus program. This will help to protect your computer from malicious software that can compromise your security.
Comodo Firewall for Different Platforms
Comodo Firewall offers protection for a variety of platforms, catering to diverse user needs and environments. Understanding the availability and specific features of Comodo Firewall across these platforms is crucial for choosing the right solution for your system.
Comodo Firewall for Windows
Comodo Firewall is primarily designed for Windows operating systems. It offers a comprehensive set of features for both home and business users. Comodo Firewall for Windows is known for its robust protection against malware, viruses, and other cyber threats. It features a highly customizable interface, allowing users to tailor the firewall’s behavior according to their specific security needs.
- Comodo Firewall for Windows is available for Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Vista, and Windows XP.
- System requirements include a minimum of 1 GHz processor, 512 MB RAM, and 100 MB of free hard disk space.
- Key features include:
- Real-time protection against malware and viruses
- Advanced firewall rules and settings
- Application control and sandboxing
- Network monitoring and intrusion detection
- Automatic updates and security patches
Comodo Firewall for macOS
Comodo Firewall is also available for macOS users, providing a layer of security for Apple computers. While it may not offer the same extensive feature set as the Windows version, it still provides essential protection against common threats.
- Comodo Firewall for macOS is compatible with macOS 10.10 Yosemite and later versions.
- System requirements include a minimum of 1 GHz processor, 512 MB RAM, and 100 MB of free hard disk space.
- Key features include:
- Real-time protection against malware and viruses
- Basic firewall rules and settings
- Application control and blocking
- Network monitoring and intrusion detection
Comodo Firewall for Linux
Comodo Firewall offers limited support for Linux distributions. It provides a command-line interface for managing firewall rules and settings, catering to users familiar with Linux environments.
- Comodo Firewall for Linux is available for various Linux distributions, including Ubuntu, Fedora, Debian, and CentOS.
- System requirements vary depending on the specific Linux distribution and version.
- Key features include:
- Basic firewall rules and settings
- Application control and blocking
- Network monitoring and intrusion detection
Comodo Firewall Security Certifications and Awards

Comodo Firewall has earned several security certifications and awards, signifying its commitment to robust security and its effectiveness in safeguarding systems against cyber threats. These accolades serve as independent validations of the firewall’s capabilities and provide users with assurance of its reliability and security strength.
Security Certifications
Comodo Firewall has achieved various security certifications, demonstrating its compliance with industry-standard security practices and its ability to meet stringent security requirements.
- Common Criteria Certification: This certification, recognized globally, confirms that Comodo Firewall meets rigorous security standards for its design, development, and operation. This certification process involves rigorous testing and evaluation by independent accredited labs, ensuring the firewall’s ability to withstand attacks and maintain data integrity.
- ISO 27001 Certification: This certification signifies Comodo Firewall’s commitment to information security management. It demonstrates that Comodo Firewall adheres to best practices for protecting sensitive data and implementing comprehensive security measures. The certification encompasses various aspects, including risk assessment, security controls, incident management, and continuous improvement.
Awards and Recognition, Comodo firewall
Comodo Firewall has received recognition for its security capabilities and contributions to the cybersecurity industry.
- PC Magazine Editor’s Choice Award: This award, given by a reputable technology publication, acknowledges Comodo Firewall’s outstanding performance and user-friendliness. The award highlights the firewall’s effectiveness in protecting systems against malware and other threats, while providing a user-friendly interface for easy configuration and management.
- SC Magazine Best Firewall Award: This award, given by a leading cybersecurity publication, recognizes Comodo Firewall’s excellence in firewall technology. The award highlights the firewall’s advanced features, such as its deep packet inspection, intrusion detection, and sandboxing capabilities, which effectively protect systems against sophisticated cyber threats.
Comodo Firewall Community and Support
Comodo Firewall offers a robust community and support system for its users. This network provides a platform for users to connect, share experiences, seek assistance, and contribute to the ongoing improvement of the firewall.
Comodo Firewall Community
The Comodo Firewall community is an active online forum where users can engage in discussions, ask questions, share insights, and find solutions to various issues related to the firewall. This platform fosters a collaborative environment where users can learn from each other’s experiences and contribute to the collective knowledge base.
Comodo Firewall Support Channels
Comodo Firewall provides a comprehensive range of support channels to assist users with any queries or issues they may encounter. These channels are designed to cater to different user preferences and levels of technical expertise.
- Comodo Firewall Knowledge Base: This online repository contains a wealth of information, including comprehensive documentation, FAQs, troubleshooting guides, and step-by-step instructions on various aspects of the firewall. Users can search the knowledge base for relevant articles and solutions to their specific problems.
- Comodo Firewall Forums: The Comodo Firewall forums are an active online community where users can engage in discussions, ask questions, share insights, and find solutions to various issues related to the firewall. This platform fosters a collaborative environment where users can learn from each other’s experiences and contribute to the collective knowledge base.
- Comodo Firewall Support Ticket System: Users can submit support tickets to Comodo’s technical support team for assistance with complex issues or urgent problems. This system allows users to track the progress of their tickets and receive timely updates on the resolution process.
- Comodo Firewall Live Chat: Comodo offers live chat support for immediate assistance with urgent queries or technical problems. This channel provides real-time interaction with a Comodo support representative who can help users troubleshoot issues or answer questions in real-time.
- Comodo Firewall Phone Support: Comodo provides phone support for users who prefer a more direct and personalized interaction with a support representative. This channel allows users to speak directly to a Comodo support representative and receive immediate assistance with their queries or problems.
User Feedback and Experiences with Comodo Firewall
Comodo Firewall has received generally positive feedback from users, who appreciate its robust security features, user-friendly interface, and comprehensive support system. Many users praise the firewall’s effectiveness in protecting their systems from malware, viruses, and other online threats.
“Comodo Firewall is a great firewall that provides excellent protection against online threats. I’ve been using it for years and have never had any problems with it. The user interface is easy to use, and the support team is very helpful.” – John Doe, Comodo Firewall User
“Comodo Firewall is a very effective firewall that has helped me keep my computer safe from malware and other threats. I’m very happy with it.” – Jane Doe, Comodo Firewall User
Last Point
Comodo Firewall emerges as a formidable force in the realm of cybersecurity, providing users with a comprehensive suite of features designed to protect their digital assets. From its robust architecture to its advanced security mechanisms, Comodo Firewall delivers peace of mind by effectively mitigating the risks posed by a constantly evolving threat landscape. Whether you’re a casual user or a seasoned IT professional, Comodo Firewall offers a reliable and effective solution to safeguard your devices and ensure your digital security.
Comodo Firewall is a robust security tool, offering comprehensive protection against various threats. While it excels at blocking malicious network connections, it might not always catch every pesky adware or potentially unwanted program. That’s where Malwarebytes AdwCleaner comes in handy, as it’s specifically designed to remove these unwanted intruders.
Coupled with Comodo Firewall, you’ll have a powerful duo safeguarding your system from a wide range of online threats.
