Advanced port scanners are powerful tools that go beyond basic network analysis, offering deep insights into the vulnerabilities and security posture of systems and networks. These scanners delve into the intricacies of network protocols, employing sophisticated techniques to uncover hidden vulnerabilities and potential security risks.
Table of Contents
By examining the TCP/IP stack, analyzing network traffic patterns, and identifying running services, advanced port scanners provide a comprehensive understanding of a network’s security landscape. This information empowers security professionals to identify potential attack vectors, implement appropriate security measures, and proactively mitigate risks.
Introduction to Advanced Port Scanners
Advanced port scanners are specialized tools that go beyond basic network scanning capabilities, providing comprehensive and detailed information about network vulnerabilities. They play a crucial role in network security by helping security professionals identify potential security risks and weaknesses that could be exploited by attackers.
Advanced port scanners are designed to provide a deeper understanding of network security posture than basic scanners. They offer a range of features that go beyond simply identifying open ports, enabling security professionals to perform more in-depth analysis and vulnerability assessments.
Key Features of Advanced Port Scanners
Advanced port scanners are distinguished from basic scanners by their advanced features that enhance their capabilities and effectiveness in network security analysis. These features include:
- Vulnerability Scanning: Advanced scanners can go beyond identifying open ports and detect specific vulnerabilities associated with the identified services. They use databases of known vulnerabilities and exploit patterns to assess the risk level of each identified port.
- Operating System (OS) Fingerprinting: By analyzing the responses from target devices, advanced scanners can identify the operating system running on each device, providing valuable information for vulnerability assessment and targeted exploitation.
- Service Detection and Version Identification: Beyond identifying open ports, advanced scanners can identify the specific services running on each port, along with their versions. This allows for more accurate vulnerability assessments, as different versions of the same service can have different vulnerabilities.
- Network Mapping and Visualization: Advanced scanners can create detailed maps of the network topology, illustrating the connections between devices and services. This visualization can help security professionals understand the network structure and identify potential security risks.
- Scripting and Automation: Advanced scanners often offer scripting capabilities that allow security professionals to automate repetitive tasks, such as scanning multiple targets or generating customized reports. This can significantly improve efficiency and reduce manual effort.
- Stealth Scanning: Advanced scanners can use techniques like stealth scanning to minimize the chances of detection by firewalls or intrusion detection systems. This can be crucial for performing security assessments without disrupting normal network operations.
Advantages of Using Advanced Port Scanners
Advanced port scanners offer several advantages for network security professionals:
- Comprehensive Vulnerability Assessment: Advanced scanners can identify a wider range of vulnerabilities than basic scanners, providing a more comprehensive understanding of the network’s security posture.
- Targeted Security Measures: By identifying specific vulnerabilities and their associated risks, advanced scanners enable security professionals to implement targeted security measures, addressing the most critical vulnerabilities first.
- Improved Threat Detection: Advanced scanners can help detect potential threats that might not be visible to basic scanners, such as hidden services or malicious activity.
- Enhanced Network Security: By identifying and addressing vulnerabilities, advanced scanners help improve overall network security, reducing the risk of attacks and data breaches.
Disadvantages of Using Advanced Port Scanners
While advanced port scanners offer significant advantages, there are also some potential disadvantages:
- Potential for Network Disruption: Intensive scanning can potentially disrupt network traffic, especially in high-traffic environments. It is crucial to use advanced scanners responsibly and minimize their impact on network performance.
- False Positives: Advanced scanners can sometimes generate false positives, identifying vulnerabilities that do not actually exist. This can lead to unnecessary security measures and wasted resources.
- Complexity: Advanced scanners can be complex to use and require a certain level of expertise to configure and interpret the results. This can be a challenge for security professionals with limited experience.
- Legal and Ethical Considerations: It is essential to use advanced port scanners responsibly and ethically. Unauthorized scanning of networks can be illegal and unethical, and it is crucial to comply with all applicable laws and regulations.
Types of Advanced Port Scanners
Advanced port scanners are powerful tools that go beyond basic port scanning, offering a wide range of features and capabilities. These tools can be categorized based on their functionality, allowing security professionals to choose the right scanner for their specific needs.
Vulnerability Scanners
Vulnerability scanners are a type of advanced port scanner that focuses on identifying potential security weaknesses in systems and applications. They go beyond simply checking if a port is open; they actively probe for known vulnerabilities and security misconfigurations. This information can be used to prioritize remediation efforts and improve the overall security posture of a network.
- Example: Nessus, OpenVAS, Qualys
Stealth Scanners
Stealth scanners are designed to minimize their network footprint, making them less detectable by intrusion detection systems (IDSs). They use techniques like TCP SYN scanning, which only sends a SYN packet to initiate a connection without fully establishing it. This reduces the risk of triggering an alert, making them ideal for reconnaissance or penetration testing.
- Example: Nmap (with the -sS flag), Zmap
Network Mappers
Network mappers are advanced port scanners that focus on discovering and mapping the structure of a network. They go beyond simply identifying open ports; they can also identify the operating system running on each device, the services running on each port, and the network topology. This information is invaluable for network administrators and security professionals who need to understand the layout and security posture of their network.
- Example: Nmap (with the -T4 flag), Angry IP Scanner
Protocol Analyzers
Protocol analyzers, also known as packet sniffers, are advanced port scanners that capture and analyze network traffic. They provide detailed information about the communication between devices, including the protocols used, the data exchanged, and the timing of each packet. This information can be used to identify network anomalies, troubleshoot network issues, and analyze security threats.
- Example: Wireshark, tcpdump
Specialized Scanners
In addition to these general categories, there are also specialized port scanners designed for specific purposes. For example, some scanners are designed for scanning specific types of devices, such as web servers or databases. Others are designed to identify specific vulnerabilities, such as SQL injection or cross-site scripting.
- Example: Nikto (for web servers), SQLMap (for SQL injection vulnerabilities)
Techniques Used in Advanced Port Scanning
Advanced port scanning techniques go beyond simple port checks and delve into analyzing network responses to gather more detailed information about target systems. These techniques help identify vulnerabilities, understand system configurations, and even infer the operating system and applications running on the target.
TCP/IP Stack Fingerprinting
TCP/IP stack fingerprinting is a technique used to identify the operating system of a target system by analyzing its response to specially crafted TCP/IP packets. Different operating systems implement the TCP/IP stack in slightly different ways, leading to variations in how they handle specific TCP/IP packets. By sending these packets and observing the responses, an attacker can identify the specific operating system version.
Advantages
- Provides information about the target’s operating system.
- Can be used to identify vulnerabilities specific to certain operating systems.
Limitations
- Requires sending specially crafted packets, which can be detected by intrusion detection systems (IDSs).
- Operating systems can be configured to mask their fingerprints, making it difficult to identify them.
- Some operating systems may respond in unexpected ways, making it difficult to interpret the results.
Banner Grabbing
Banner grabbing is a technique used to retrieve information about services running on a target system. When a connection is established to a port, many services send a banner, which is a short message containing information about the service, its version, and other details. Banner grabbing involves sending a connection request to a specific port and then analyzing the banner returned by the service.
Advantages
- Provides information about the services running on the target system.
- Can be used to identify vulnerabilities specific to certain service versions.
Limitations
- Some services may not send banners, or they may send generic banners that do not reveal much information.
- Banner grabbing can be blocked by firewalls or other security measures.
Service Detection
Service detection is a technique used to determine which services are running on a target system. This technique involves sending specially crafted packets to different ports and analyzing the responses to identify the service running on each port. This can be done by examining the response headers, payload, or other characteristics of the response.
Advantages
- Provides a comprehensive list of services running on the target system.
- Can be used to identify vulnerabilities specific to certain services.
Limitations
- Some services may not respond to specific probes, making it difficult to identify them.
- Service detection can be blocked by firewalls or other security measures.
Applications of Advanced Port Scanners
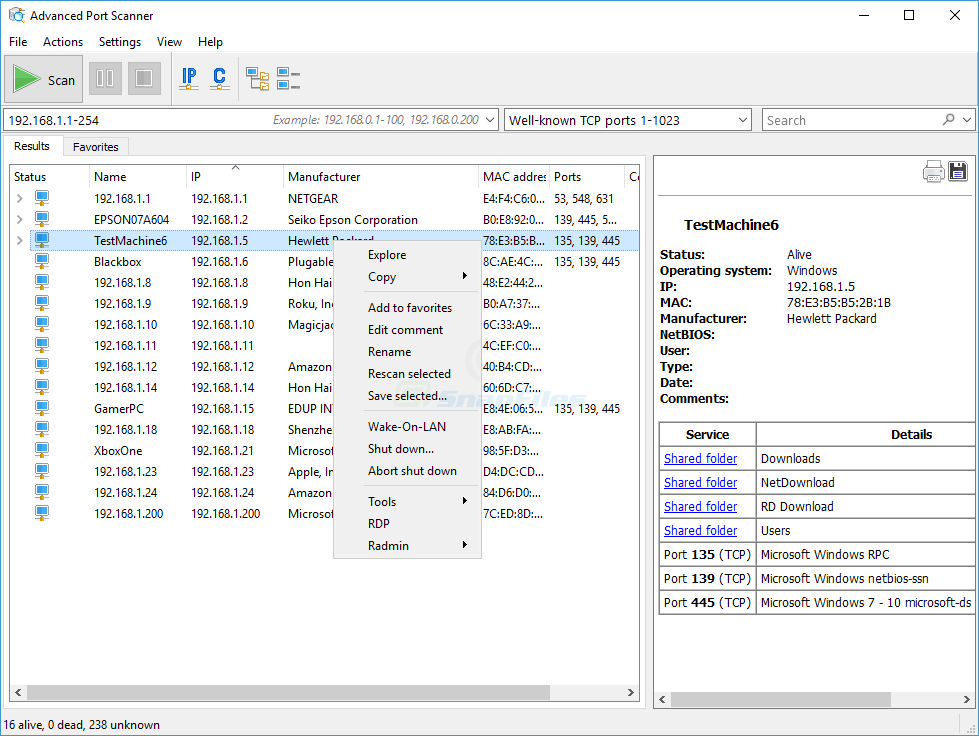
Advanced port scanners are powerful tools that go beyond basic port discovery, offering sophisticated capabilities for network security professionals. They are essential for a wide range of security tasks, enabling comprehensive assessments, proactive defense, and intelligent network management.
Vulnerability Assessment
Vulnerability assessments aim to identify potential weaknesses in systems and applications that could be exploited by attackers. Advanced port scanners play a crucial role in this process by:
* Identifying Open Ports and Services: They scan for open ports and running services, providing a comprehensive inventory of potential attack vectors.
* Detecting Vulnerable Services: They can identify known vulnerabilities in specific services by analyzing the versions and configurations of software running on the target system.
* Exploiting Weaknesses: Some advanced scanners offer features to exploit vulnerabilities and assess their impact, providing valuable insights for remediation efforts.
For instance, an advanced scanner might identify an outdated version of an FTP server running on a specific port. This information helps security professionals prioritize patching or upgrading the server to address the vulnerability.
Penetration Testing
Penetration testing simulates real-world attacks to assess the security posture of a system or network. Advanced port scanners are indispensable tools for penetration testers, allowing them to:
* Discover Attack Surfaces: They help identify the network’s attack surface by mapping open ports, services, and potential entry points.
* Identify and Exploit Vulnerabilities: Advanced scanners can perform targeted scans to discover and exploit known vulnerabilities, mimicking the techniques used by real attackers.
* Assess the Effectiveness of Security Controls: They can evaluate the effectiveness of firewalls, intrusion detection systems, and other security measures by testing their ability to block malicious traffic.
A penetration tester might use an advanced scanner to test the security of a web server. By simulating a common SQL injection attack, the tester can determine if the server is vulnerable and assess the impact of the attack.
Network Mapping
Network mapping is the process of identifying and documenting the devices and connections within a network. Advanced port scanners are invaluable for network mapping by:
* Discovering Network Devices: They can identify all devices connected to the network by scanning for active hosts and services.
* Creating Network Diagrams: The information gathered from scans can be used to create accurate network diagrams, providing a visual representation of the network infrastructure.
* Identifying Network Segmentation: They can help identify network segments and determine the flow of traffic within the network.
A network administrator might use an advanced scanner to map the network infrastructure of a large organization. The resulting network diagram can help identify potential security risks and optimize network performance.
Ethical Considerations of Advanced Port Scanning
Advanced port scanning, while a powerful tool for network security professionals, comes with ethical implications that require careful consideration. Misuse of these techniques can have severe consequences, ranging from privacy violations to unauthorized access to sensitive systems. It’s crucial to understand the ethical landscape and adhere to best practices to ensure responsible use.
Potential for Misuse
The power of advanced port scanning lies in its ability to uncover vulnerabilities and potential security risks. However, this same power can be misused for malicious purposes. For instance, an attacker could use advanced port scanning to identify open ports and exploit known vulnerabilities to gain unauthorized access to systems. This could lead to data breaches, system disruptions, or even financial losses.
Privacy Concerns
Advanced port scanning can inadvertently reveal information about individuals or organizations that may be considered private. For example, scanning a network for specific services could reveal the presence of certain applications or devices that might indicate sensitive activities. This information could be misused for targeted attacks or privacy violations.
Best Practices for Responsible Port Scanning, Advanced port scanner
To mitigate the ethical risks associated with advanced port scanning, it’s essential to adhere to best practices:
- Obtain Explicit Consent: Before scanning a network, obtain explicit consent from the network owner or administrator. This ensures that the scanning activity is authorized and that the network owner is aware of the potential risks involved.
- Minimize the Scope of Scanning: Limit the scope of your scan to the specific targets you need to assess. Avoid scanning entire networks unnecessarily, as this can increase the risk of unintended consequences.
- Respect Network Security Measures: Avoid attempting to bypass security measures or access restricted areas of a network. Respect the security policies of the network you are scanning.
- Use Automated Tools Responsibly: When using automated scanning tools, configure them carefully to avoid excessive traffic or unintended consequences. Regularly monitor the tools’ activity and ensure they are operating within acceptable limits.
- Document Your Actions: Keep detailed records of your scanning activities, including the dates, times, targets, and any findings. This documentation can be valuable for future reference and for demonstrating responsible use.
Legal Considerations
In many jurisdictions, unauthorized port scanning can be considered illegal. It’s crucial to understand the legal framework surrounding port scanning in your region and ensure your actions comply with all applicable laws and regulations. For example, the Computer Fraud and Abuse Act (CFAA) in the United States prohibits unauthorized access to computer systems, which could include port scanning without proper authorization.
Examples of Ethical Dilemmas
Consider a scenario where a security researcher discovers a vulnerability in a widely used web server. The researcher could use advanced port scanning to identify systems vulnerable to this exploit. However, disclosing this information could potentially lead to malicious actors exploiting the vulnerability before it is patched. This raises ethical questions about the balance between responsible disclosure and potential harm.
Advanced Port Scanning Tools and Resources
A plethora of advanced port scanning tools are available, each with its own set of features, advantages, and limitations. These tools are crucial for security professionals, penetration testers, and network administrators who need to perform in-depth network analysis and vulnerability assessments.
Advanced Port Scanning Tools
Here’s a table showcasing some popular advanced port scanning tools:
| Tool Name | Key Features | Pros | Cons | Availability |
|---|---|---|---|---|
| Nmap | – Comprehensive port scanning – OS detection – Service version identification – Scripting capabilities – Network mapping |
– Highly versatile and customizable – Open-source and free – Extensive documentation and community support – Powerful scripting capabilities |
– Can be complex for beginners – Requires some technical expertise to use effectively |
Available on Linux, macOS, and Windows |
| Masscan | – Extremely fast port scanning – Supports multiple target types – Can scan entire IP ranges quickly |
– Very fast scanning speeds – Highly efficient for large-scale scans |
– Limited features compared to Nmap – Less customizable |
Available on Linux |
| Acunetix WVS | – Web application vulnerability scanning – Comprehensive port scanning – Automated vulnerability detection |
– User-friendly interface – Comprehensive vulnerability reporting – Integrates with other security tools |
– Commercial software (paid subscription) – Can be resource-intensive for large scans |
Available on Windows and Linux |
| OpenVAS | – Vulnerability assessment and management – Port scanning – Vulnerability detection and reporting |
– Open-source and free – Provides detailed vulnerability information – Integrates with other security tools |
– Requires some technical expertise to configure and use – Can be resource-intensive for large scans |
Available on Linux, macOS, and Windows |
| Nessus | – Comprehensive vulnerability scanning – Port scanning – Network discovery – Compliance reporting |
– Comprehensive vulnerability coverage – User-friendly interface – Integrates with other security tools |
– Commercial software (paid subscription) – Can be resource-intensive for large scans |
Available on Windows, Linux, and macOS |
Resources for Further Information
– Nmap Project: [https://nmap.org/](https://nmap.org/)
– Masscan Project: [https://github.com/robertdavidgraham/masscan](https://github.com/robertdavidgraham/masscan)
– Acunetix Website: [https://www.acunetix.com/](https://www.acunetix.com/)
– OpenVAS Project: [https://www.openvas.org/](https://www.openvas.org/)
– Tenable Website: [https://www.tenable.com/](https://www.tenable.com/)
Advanced Port Scanning in the Context of Network Security
Advanced port scanning plays a crucial role in identifying vulnerabilities and potential security risks within a network. By systematically probing open ports, advanced port scanners can uncover weaknesses that malicious actors could exploit to gain unauthorized access.
Vulnerability Identification
Advanced port scanners are essential tools for identifying vulnerabilities in network systems. They can determine which ports are open, the services running on those ports, and the versions of those services. This information can then be used to identify known vulnerabilities, such as outdated software versions or misconfigured services.
- Open Ports and Services: By scanning for open ports, advanced scanners can reveal which services are exposed to the network. This information can be used to identify potentially vulnerable services that should be patched or secured. For example, if a server is running an outdated version of a web server software on port 80, it may be vulnerable to known exploits.
- Service Versions: Advanced scanners can identify the specific versions of services running on open ports. This is crucial because older versions of software often contain known vulnerabilities that attackers can exploit. By identifying the specific version of a service, security professionals can determine if it is vulnerable and take appropriate action.
- Operating System Fingerprinting: Some advanced scanners can identify the operating system running on a target device by analyzing the responses from open ports. This information can be used to determine if the operating system is vulnerable to known exploits.
Threat Detection and Incident Response
Advanced port scanners can be used to detect threats and respond to incidents. By continuously monitoring network activity, these scanners can identify suspicious behavior, such as attempts to scan for open ports or access restricted services.
- Real-Time Monitoring: Advanced port scanners can be configured to continuously monitor network activity and alert security teams to suspicious behavior. This allows for the early detection of potential attacks and the rapid implementation of mitigation strategies.
- Incident Response: In the event of a security incident, advanced port scanners can be used to identify the source of the attack, the compromised systems, and the extent of the damage. This information is essential for effective incident response and remediation.
Security Best Practices for Using Advanced Port Scanners
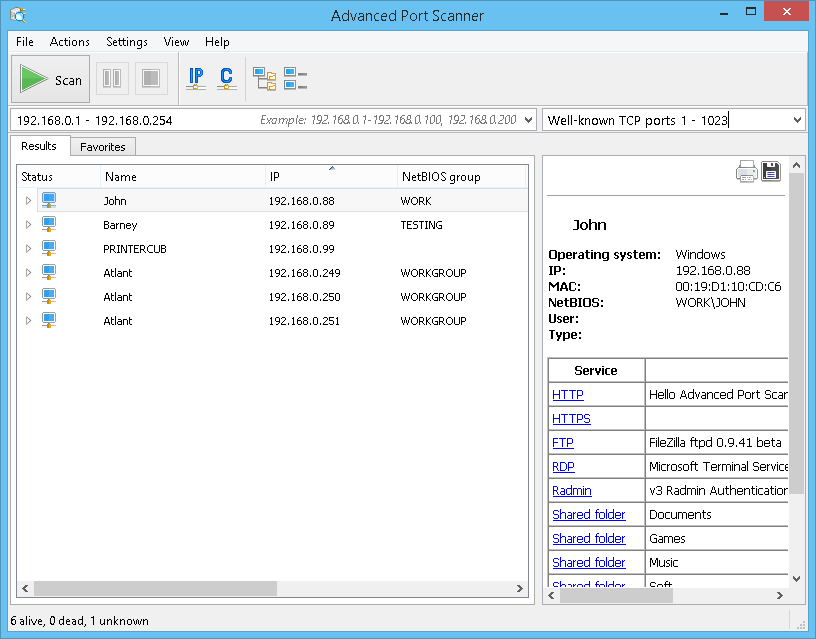
Advanced port scanners are powerful tools that can be used for various purposes, including network security assessments, penetration testing, and vulnerability identification. However, it is crucial to use these tools responsibly and ethically to avoid causing any harm or damage to systems or networks.
Using Advanced Port Scanners Responsibly
Using advanced port scanners responsibly is paramount to ensure that your actions do not negatively impact others or compromise their security. Here are some key best practices to keep in mind:
- Obtain explicit permission: Before scanning any network or system, always obtain explicit permission from the owner or administrator. This is a fundamental ethical principle that demonstrates respect for others’ privacy and security.
- Respect privacy: When scanning networks, avoid targeting personal devices or systems without explicit consent. Focus on infrastructure or publicly accessible systems that are relevant to your security assessment or research.
- Avoid malicious intent: Use advanced port scanners for legitimate purposes such as security assessments, penetration testing, or vulnerability identification. Never use them for malicious activities like denial-of-service attacks or data theft.
- Minimize impact: When scanning networks, use appropriate scan parameters to minimize the impact on network performance. Consider factors like scan speed, number of ports scanned, and the frequency of scans.
Configuring Advanced Port Scanners
Proper configuration of advanced port scanners is essential to avoid accidental damage or misuse. Here are some important configuration considerations:
- Scan rate: Set the scan rate to a reasonable level to avoid overwhelming the target system. This is particularly important when scanning large networks or systems with limited resources.
- Timeout settings: Configure appropriate timeout settings to prevent scans from hanging or consuming excessive resources. This helps ensure that the scanner operates efficiently and does not disrupt network operations.
- Target filtering: Use target filtering options to specify the range of IP addresses or hosts to scan. This allows you to focus your efforts on specific systems or networks, reducing the risk of accidentally scanning unintended targets.
- Port range: Define the specific range of ports to scan. This helps you focus on ports relevant to your assessment, reducing the time and resources required for scanning.
- Scan types: Choose appropriate scan types based on your assessment objectives. Different scan types offer varying levels of intrusiveness and can impact network performance.
Logging and Reporting
Maintaining accurate logs and reports is crucial for tracking your scanning activities and demonstrating responsible use.
- Detailed logs: Keep detailed logs of all scanning activities, including the date, time, target IP addresses, ports scanned, and scan results. This helps you track your work, identify potential issues, and provide evidence of responsible use.
- Reporting: Generate clear and concise reports summarizing your scanning findings. Include details about vulnerabilities discovered, potential risks, and recommendations for remediation.
Future Trends in Advanced Port Scanning
The field of advanced port scanning is constantly evolving, driven by the rapid advancements in technology and the ever-changing landscape of cybersecurity. As networks become more complex and sophisticated, port scanning techniques are adapting to keep pace. Emerging technologies like machine learning and artificial intelligence are playing a significant role in shaping the future of advanced port scanning.
The Rise of Machine Learning and AI in Port Scanning
Machine learning and artificial intelligence are poised to revolutionize advanced port scanning by automating tasks, enhancing accuracy, and providing deeper insights.
- Automated Port Scanning and Vulnerability Identification: Machine learning algorithms can analyze vast amounts of data from network traffic and identify patterns that indicate open ports, vulnerabilities, and potential security risks. This automation streamlines the port scanning process and frees up security professionals to focus on more strategic tasks.
- Adaptive Port Scanning Techniques: AI-powered port scanners can adapt to changing network conditions, dynamically adjusting scanning parameters and strategies based on real-time data analysis. This adaptive approach enhances the effectiveness of port scans by circumventing security measures and identifying hidden vulnerabilities.
- Predictive Port Scanning: Machine learning models can be trained on historical data to predict future port scanning activities. This predictive capability allows organizations to proactively identify potential threats and implement preventative measures before attacks occur.
The Future of Advanced Port Scanning Tools and Techniques
As technology continues to advance, we can expect to see significant changes in the tools and techniques used for advanced port scanning.
- Cloud-Based Port Scanning: Cloud computing platforms offer scalable and flexible solutions for port scanning. Cloud-based tools can leverage distributed computing power to perform large-scale scans and analyze massive datasets, enabling organizations to conduct more comprehensive security assessments.
- Integration with Security Information and Event Management (SIEM): Advanced port scanners will seamlessly integrate with SIEM systems, providing real-time insights into network activity and enabling automated threat detection and response. This integration will streamline security operations and enhance the overall effectiveness of security measures.
- Enhanced Reporting and Visualization: Future port scanning tools will generate detailed reports and visualizations, providing clear and actionable insights into network security posture. These advanced reporting capabilities will help organizations understand the potential risks and vulnerabilities in their network infrastructure and make informed decisions about security investments.
Conclusive Thoughts: Advanced Port Scanner
In the ever-evolving landscape of cybersecurity, advanced port scanners play a crucial role in safeguarding networks and systems. Their ability to identify vulnerabilities, assess security risks, and facilitate penetration testing makes them invaluable assets for security professionals. By understanding the intricacies of advanced port scanning techniques and tools, organizations can enhance their security posture and protect against sophisticated cyber threats.
An advanced port scanner can be a valuable tool for network administrators, helping them identify open ports and potential vulnerabilities. However, it’s important to use these tools responsibly, especially when scanning networks outside of your own. If you’re a student, you can learn more about network security and ethical hacking through resources like the Microsoft Student program.
By understanding the principles of network security, you can better utilize advanced port scanners for legitimate purposes, such as troubleshooting network issues or identifying potential security risks.
